Articles by Admin
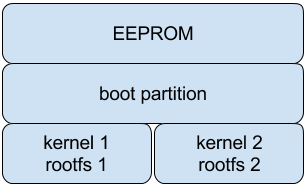
Partition layout design for embedded devices to enable image-based updates
Software updates for embedded devices are typically deployed as full image updates. There are many design considerations take into account in the partition
|
2 min read
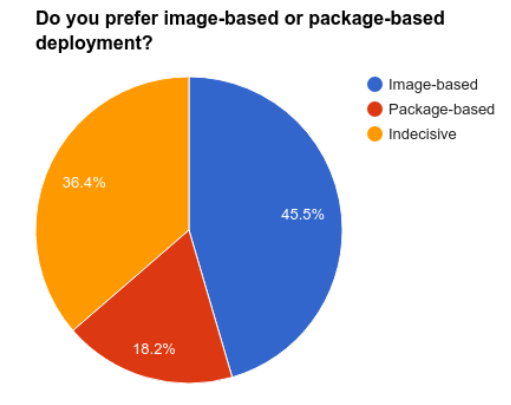
Firmware over-the-air: package-based vs image-based updates
Here at Mender.io, we did a comprehensive survey with embedded developers and what they did with devices that required software updates over-the-air (OTA).
|
1 min read
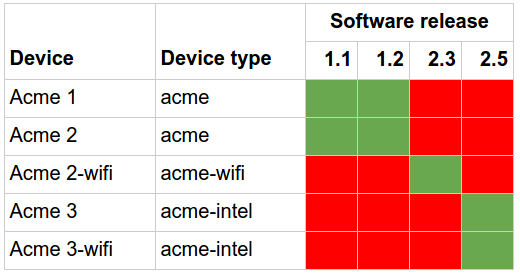
Using build information from Yocto to deploy software updates (part 2)
In our previous post, we discussed the need to check compatibility for software and devices when designing a solution to deploy software updates. We also s
|
3 min read
Using build information from Yocto to deploy software updates (part 1)
When designing an embedded or IoT product, the problem of deploying software updates to the devices in the field quickly becomes a problem. The main driver
|
1 min read
The case for over-the-air software updates and patching the Internet of Things
Embedded systems have existed since the Apollo space program - the Apollo Guidance Computer in the Lunar Module is regarded as the first embedded computer,
|
1 min read
Security updates for the Internet of Things (part 2)
Part two of two - part one is available here. The Internet of Things are: Resource constrained Field-deployed These devices are beyond the “safety” of the
|
2 min read
Security updates for the Internet of Things (part 1)
Part one of two - part two is available here. A decade ago, managing security patches was not a top priority for most IT security personnel. Vulnerable sys
|
3 min read