How to comply with ISO/SAE 21434 & UNECE R155/R156 for robust automotive cybersecurity


Software is eating the car. A modern electric vehicle (EV) runs more than 100 million lines of codes, hundreds of electronic control units (ECUs), and includes an average of 1500 semiconductor chips. Software controls everything from the infotainment system and driver assist features to engine, power, and critical safety functions.
With an expected life of over 20 years, vehicle cybersecurity is not just a top priority, but a necessity to ensure safety.
To ensure the consideration and implementation of comprehensive cybersecurity in vehicles, International Organization for Standardization (ISO) 21434 and United Nations Economic Commission for Europe (UNECE) R155/156 came into force successively. Although passing the regulations assures customers that security measures are appropriately applied, it simultaneously poses significant challenges for automotive manufacturers and OEMs to certify compliance.
ISO 21434 : Managing cyber risks
ISO 21434 introduces a framework for managing cybersecurity risks, including fostering a cybersecurity culture, organizational and governance issues, project dependencies, and continuous maintenance.The 85-page document states engineering requirements for cybersecurity implementation. ISO 21434 covers all electronic systems and software devices within a vehicle and encompasses their connectivity to external systems throughout the entire lifecycle. Throughout concept, product development, production, operation, maintenance, and decommissioning, automotive and OEM manufacturers are responsible for ensuring cyber risks are monitored, detected, and mitigated.
UNECE R155/156: Requiring a certified cybersecurity management system
The United Nations Economic Commission for Europe (UNECE) adopted UNECE R155 in 2020, mandating a certified cybersecurity management system (CSMS) as a prerequisite for automotive manufacturers to achieve vehicle type approval and sell new vehicle types. UNECE R155 explicitly references and overlaps with the ISO 21434 standard.
Learn more about the latest cybersecurity requirements for the automotive industry. Download the regulatory overview.
The need for secure over-the-air (OTA) software updates
To achieve cybersecurity compliance in the automotive industry, manufacturers and OEMs must understand and implement the latest cybersecurity requirements. At the core, managing cybersecurity for vehicles throughout their lifecycle requires long-term security risk monitoring, troubleshooting, and remediation. Due to the rapidly expanding codebase and increasing complexity of modern cars, the importance of robust, secure, and fail-safe over-the-air (OTA) software updates as a necessity for mitigating cybersecurity vulnerabilities goes without saying.
Security patches, maintenance releases, new features, and more – OTA software updates play a critical role in managing modern vehicles. However, releasing an update to vehicle software can also be used as an attack vector, requiring its own cyber risk management. For OTA software updates, manufacturers should implement a comprehensive security-by-design system covering three main components:
- Campaign management: Managing the vehicle software update to be deployed
- OTA software update delivery: Securely deploying software update to the vehicles
- In-vehicle flashing: Reprogramming and validating the devices or system of devices targeted by the update campaign
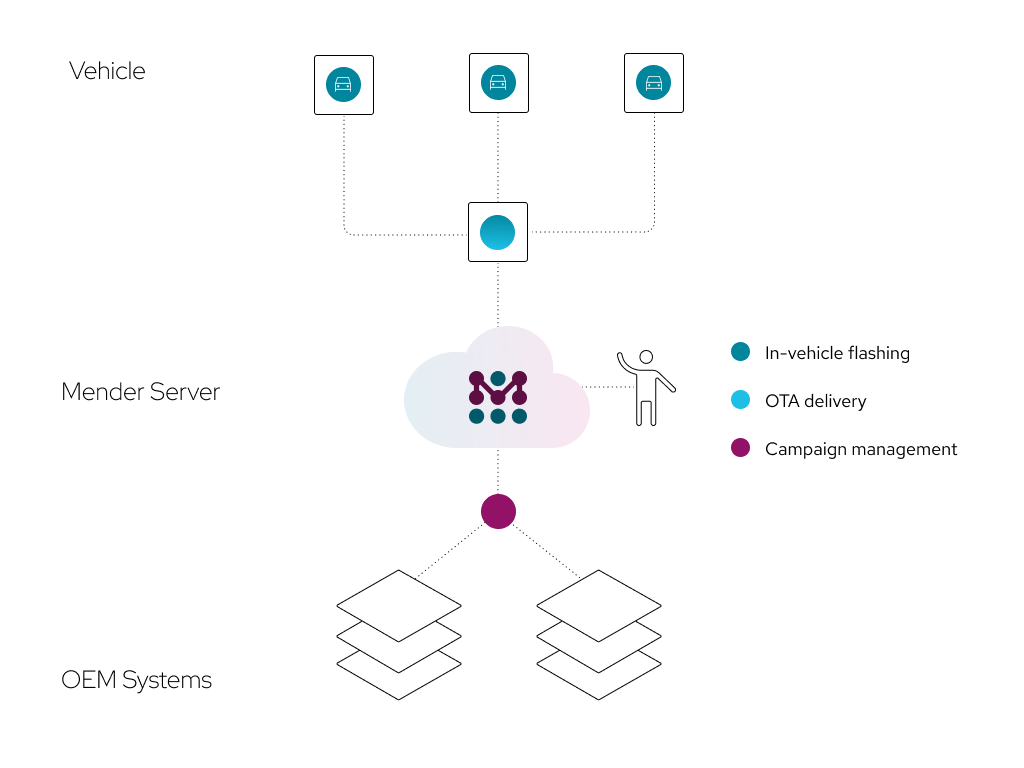
Campaign management
Campaign management focuses on defining and preparing the software update. In campaign management, server-side security is essential. On the server side, each software update has the potential to significantly impact an entire vehicle fleet; thus, a bad actor or even error on the server side of the update process poses significant cyber risk that must be managed.
For secure OTA software updates, the process and mechanism should leverage a defense-in-depth security strategy. A defense-in-depth security model restricts the impact of a cyber attack on any level, preventing a catastrophic incident. To protect the server and implement a defense-in-depth security strategy, trust must be ensured across three pillars: people, devices, and software.
People play a primary role in both cybersecurity and creating cyber risks. To manage trust across the people factor, OTA software updates should encomposs cybersecurity best practices. Secure authentication and authorization, for example, are critical. Ideally, all users accessing should be authenticated with two- or multiple-factor authentication and a one-time password token. No user accounts should be left unmanaged, and role-based access control should be in place to grant the necessary permissions.
Devices and software should also be set up to prevent cyber attacks or unauthorized usage. DoS protection against malicious attacks and encrypted binary storage can strengthen security. If suspicious activity is detected, software bill of materials and auditing logs should be possible to identify the root cause and create a remediation plan.
Over-the-air delivery
The security of OTA is essential not only because it is required to deliver security patches and updates in an efficient and scalable manner but also because the process itself can pose significant threats when done inappropriately.
Secure transport layer security (TLS) should implemented mutually on both the server and client sides. If mutual TLS is not possible, preauthorizing devices with a list of trusted public keys or accepting devices on their first requests can be alternatives. As an additional security layer, private keys stored in a hardware security module (HSM) or trusted platform module (TPM) are critical against malicious physical access to the device.
In-vehicle flashing
Externally, anything can happen in the vehicle’s environment during a OTA software update. For example, an internet disconnection, power outage, or version inconsistency can lead to incomplete updates, damaged vehicles, expensive recalls, and poor customer satisfaction.
To ensure vehicles are updated safely and seamlessly, atomic updates and automatic roll-back should be mandatory. Atomic updates and automatic roll-back ensures vehicles are never left in an intermediate, half-updated, or unpredictable state.
If the complete server infrastructure is compromised, enabling code signing with the verification of public keys should be the backup for the security or quality assurance team to achieve the highest level of security. Leveraging native diagnositic and update tools within the process adds another level of visibity and security for the vehicle update.
Securing the software-defined vehicle
"At the moment, impacted vehicles are generally wide open to these sorts of attacks. The only proper fix would be to introduce cryptographic protections to CAN messages...This could be done via a software update."
The Car Thieves Using Tech Disguised Inside Old Nokia Phones and Bluetooth Speakers, VICE
Stopping a vehicle on the highway, exploiting server-side vulnerabilities, even stealing cars – ethical hackers, bad actors, and cyber adversaries continue to target the connected car to prove a point. Cybersecurity must be embedded throughout the vehicle – secure by design. And to facilitate vehicle cybersecurity, manufacturers and OEMs require a secure and robust OTA software update mechanism.
In the case of auto theft impacting numerous manufacturers and even more vehicles, the fix could be as simple as a software update.
Quick checklist: Best practices for OTA software updates in the automotive industry
Quickly assess how your OTA software updates compare. This high-level checklist covers key capabilities for secure and robust OTA software updates.
Campaign management
- Secure user authentication and authorization
- Availability and denial-of-service (DoS) protection
- Secure binary storage
- Audit log
- Software bill of materials
Over-the-air delivery
- Secure transport layer security (TLS) communication
- Secure client authentication
- Support for hardware security module (HSM) and trusted platform module (TPM)
In-vehicle flashing
- Seamless A/B updates
- End-to-end cryptographic code signing
- Use native flashing tools
Want to learn in detail how to fulfill the security requirements in the checklist? Read the regulatory overview here.
Keep reading
To dive deeper into over-the-air updates for the automotive industry, try these articles:
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.



