We are excited to release Mender 2.2!
Mender 2.2 improves support for large-scale deployments and security.
The key features of Mender 2.2 are covered below, and you can see the detailed items in the Mender 2.2.0 release notes.
Commercial features
With the release of Mender 2.2, we also launch two new commercial plans for Mender. There are now three options to use Mender:
- Open Source - The core features of Mender, all under the Apache License v2.
- Professional - Hosted as a service with commercial value-add features. Usage-based pricing. Previously known as Hosted Mender.
- Enterprise - Hosted as a service or on-premise (at your option), with commercial value-add features, SLA, support and custom, predictable pricing.
You can read more about the plans and pricing at the Mender.io website.
New features and improvements will be added to all plans in each new Mender release. In general, increased stability and core functionality will be added to Open Source, whereas features enabling larger scale and higher levels of security will be added to the commercial plans. The following sections cover the new commercial features available in the Professional and Enterprise plans, and the Open Source features are covered below these.
Robust delta updates: Reduced network usage
The network is a scarce and expensive resource in many connected device projects. For example, popular long-range networks like 3G/4G are usually metered, typically priced at $50 - $200 per GB transferred, depending on location and scale. In addition comes data transfer costs on the cloud side. Even when using higher data-rate networks like WiFi, obtaining strong and stable connectivity to transfer large amount of data can be difficult.
Reducing the data consumed to the software update process can be addressed in several ways. The quickest way is to only update individual applications or files, for example executables, configuration files or python scripts. This method is supported in Mender through application-based Update Modules. Inherently this approach does not allow for system updates. Robustness and consistency across devices may also be at risk for such type of updates.
This is why Mender 2.2 introduces Robust delta updates. With this feature, you can generate a binary delta between two rootfs-image Mender Artifacts (.mender files) and only deploy this delta for your update process. The delta only contains the binary difference between the two Mender Artifacts, which typically leads to network savings of 70-90% (depending on the changes made). Mender Robust delta updates addresses both the need for reduced data consumption and robustness and consistency across devices.
Robustness is ensured with the delta update process supporting atomic update, integrity checks, rollback and signature verification -- just like the dual A/B full image update process in Mender always has!
Besides drastically reducing network usage, using delta updates also leads to a much faster update process when the network is the bottleneck. But even in situations with "unlimited" network access, delta updates will make the update process faster by reducing the amount of storage writes.
The exact impact is environment-specific, so we recommend you try it out yourself!
Phased rollout: Gradually roll out an update
Deploying to a larger scale customer environment with thousands or tens of thousands of devices, can pose a significant risk of something going wrong.
Regardless how well tested the software and update process is, you will only know how well the deployment works for your customers after it has been released into the field. Differences in time zones, network latency, hardware and customer usage patterns are all potential stumbling blocks preventing new software releases from behaving as expected. These factors can be impossible to predict. A failed update will result in negative customer experience and potentially high customer support costs. Worst case, collateral and brand damage might be at stake.
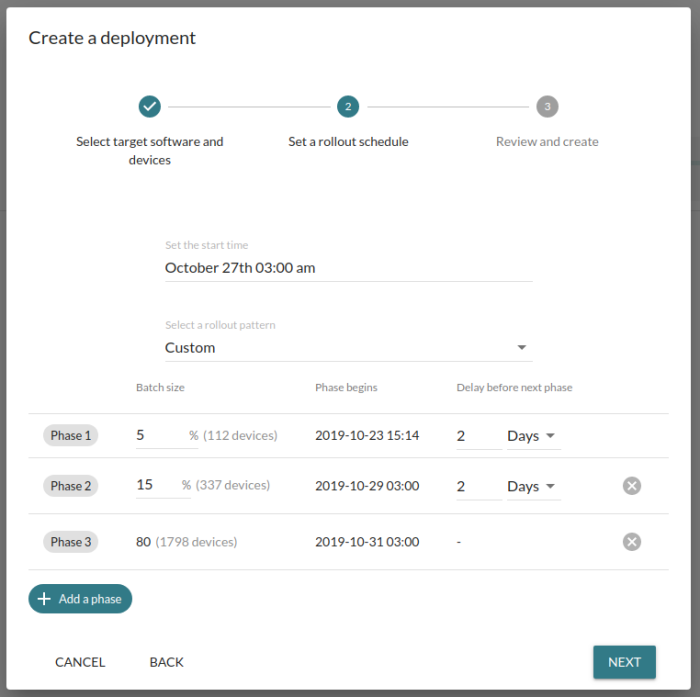
With the introduction of Phased rollout, you can greatly reduce this risk: you can divide a software update deployment into time-delayed phases with customizable share of the devices being updated in each phase. For example, deploy to 5% of the devices, wait 24 hours, then 15%, wait 24 hours and then all the remaining devices. If there are indications of problems such as update failures, higher error rates or increased customer support volumes, the update process can be aborted before it reaches a critical mass of your customers' devices -- greatly limiting negative impact during the deployment.
Mender offers completely customizable phased rollout deployment patterns, along the following axes:
- Number of phases (typical choices are 3-4)
- Share of devices in each phase (typically 5% -> 15% -> 80%)
- Time delay between the start of each phase (typically 2 days)
You can customize these settings to your needs, depending on your risk tolerance and time you have to complete the entire phased rollout.
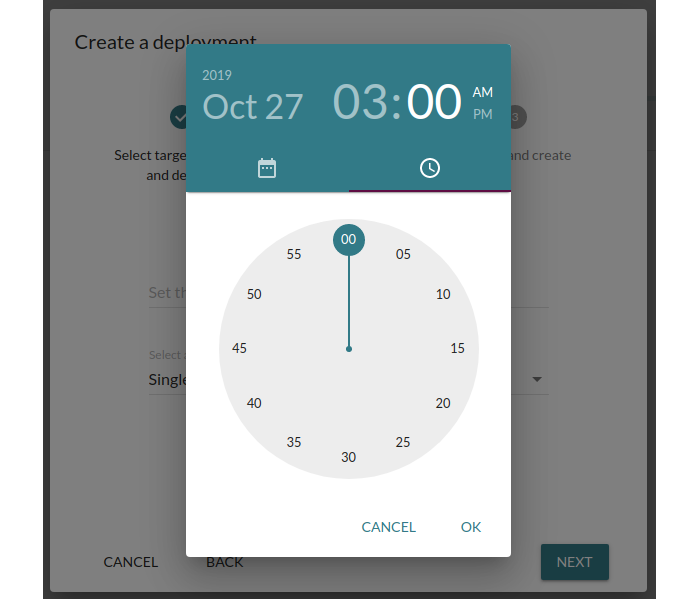
Schedule deployments: Deploy when your product is idle
Typically connected devices run through predictable cycles when they are unused or less used, for instance day versus night time. Times of idleness represent good opportunities to deploy a software update, as any downtime (such as a reboot) will most likely not affect users negatively.
Mender's focus on providing a robust update process makes it suitable for unattended updates, where no humans need to manually create the update at the right time, or observe the update reaching devices.
Scheduled deployments enable you to set a start time for the deployment into the future, such as the coming Sunday at 3am. This way, your customers are unlikely to be interrupted by the update, and your support staff does not need to be up at night to create and observe it.
Two factor authentication: Reduced risk of account compromise
Access to the OTA update server comes with great power and responsibility as it can control which software shall run on a large number of devices. If OTA update server accounts get compromised by a malicious user, severe consequences for the customer experience and brand is at stake.
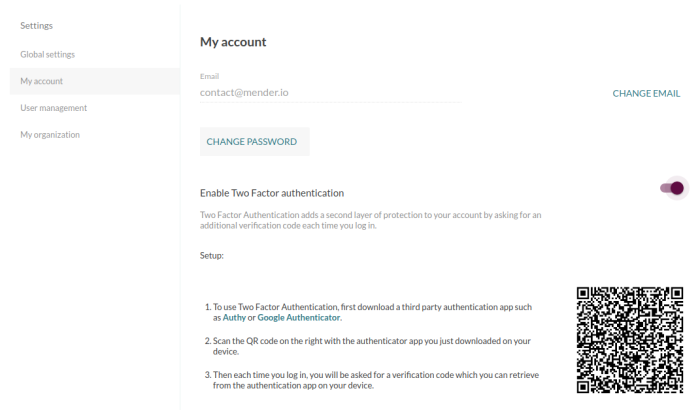
To reduce this risk Mender now supports Two factor authentication (2FA). 2FA provides each user of the Mender server an additional layer of security against account compromises. With 2FA enabled, an attacker not only would need your password, but also gain access to your smartphone.
Two factor authentication in Mender uses the industry standard One Time Password (OTP) protocol. When enabled, you are asked for an email, password and six-digit OTP code during log in. The OTP codes are generated by a smartphone app like Authy or Google Authenticator.
2FA can easily be enabled from the Mender account settings. We strongly encourage all Mender users to enable this additional layer of security.
Multi tenancy: Isolate device environments
In large scale deployments, it is often desirable to isolate devices from each other. Typical separation would be operational segmentation, such as test and production, or business segmentation among different lines of business units. Mender accommodates this need using groups. If additional isolation is desired without setting up individual Mender server instances, Multi tenancy is an easy and cost-effective option.
Multi tenancy allows you to create multiple Organizations (aka. tenants), which acts as separate environments on a single Mender server, both for users and devices. Each user is assigned to an Organization when his/her user account is created. Devices are assigned to an Organization with a "Tenant token", which is part of the Mender client configuration, a security feature to ensure devices can only authenticate with the right Organization.
Multi tenancy is only available in Mender Enterprise on-premise installations. It has already been running in production-grade environments for several years underpinning the hosted Mender service offering.
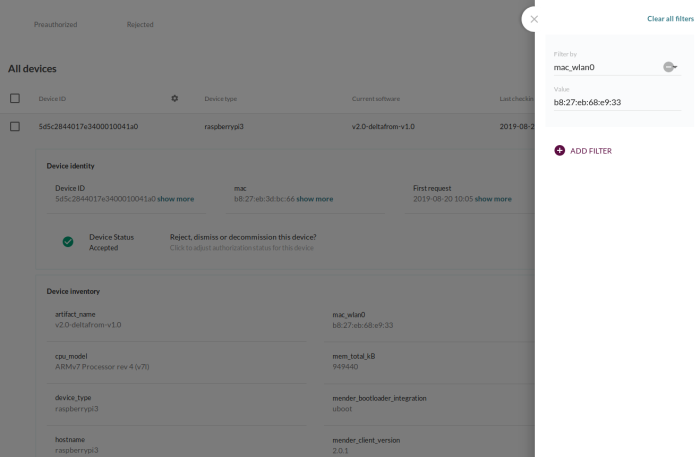
Device filtering: Find devices by inventory attributes easily
Mender discovers default inventory attributes such as MAC, IP address and OS version, and you can also easily add your own custom inventory attributes with a simple shell script or executable. The inventory then becomes available in the Mender server for informational purposes, and allows you to recognize and diagnose your devices.
With commercial plans you can filter on any inventory attribute in the user interface to quickly find devices and diagnose any issues.
Yocto Project warrior (2.7) support
With Mender 2.2, meta-mender has a new warrior branch, to fully support the warrior (2.7) release of the Yocto Project.
To check the Mender support matrix of the Yocto Project, go to the compatibility section of the documentation.
Known issue upgrading from Yocto Project thud to warrior
Please note that there is a known issue when using Mender to upgrade devices running thud to warrior. Please see the troubleshooting section for a description on how to carry out such an update of the Yocto Project version on running devices.
Raspberry Pi 4 integration for Yocto
The Raspberry Pi family of boards continue to be popular boards for the Mender community.
Mender Hub now provides an integration for the Raspberry Pi 4 on Yocto. If you have obtained a Raspberry Pi 4, make sure to test full system updates on it with the Raspberry Pi 4 Model B with the Yocto Project integration.
mender-convert 1.2.1
mender-convert, the tool that converts a Debian family disk image to a fully OTA-capable image, has received bugfixes and is now released in version 1.2.1. You can read more about mender-convert in the documentation and Mender Hub Debian family integrations.
Try Mender 2.2 now!
The easiest way to try out all features, including the commercial ones, is to sign up for Mender Professional (see below). It is free to test out!
You can also use the following links to test out the Open Source features or read more:
Sign up for Mender Professional
Mender Professional (previously known as Hosted Mender) offers all the new Mender features as a hosted service.
Mender Professional saves you time maintaining scalability, security, certificates, uptime, upgrades and compatibility of the Mender server. To use it, simply point your Mender clients to our server! The service is inexpensive and priced comparatively with the cost of self-hosting a Mender Open Source server, while giving access to more features.
Mender Professional already includes all the Mender 2.2 features!
Sign up and get your $120 free credit up to one year for Mender Professional today.
Support for your board
If you are getting started with OTA updates, or do not have time to integrate the Mender client with your board for robust A/B system updates several resources are available:
The Board Integrations category in Mender Hub is a community site to contribute, reuse and maintain Mender board integrations.
We are also happy to help with consulting services to enable verified Mender support for your board.
Share your feedback
We really appreciate your feedback on Mender, be it positive or suggestions for improvement, in the Mender Hub General Discussions forum. Your continued feedback ensures Mender will meet your needs even better in the future!
If you believe you have encountered a bug, please submit your report at the Mender JIRA issue tracker.
If you believe you have encountered a security issue, please email security@northern.tech.
We hope you enjoy the new features and look forward to hearing from you!
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.