We are happy to announce Mender 2.6 release.
Mender 2.6 comes with major architectural improvements to enable support for new use cases in Mender. The first feature to leverage the new architecture is also here: the secure Remote terminal, and more will come in future releases!
Secure Remote terminal
From the usage point of view, the new Remote terminal does exactly what you would expect: instantly creates a live remote terminal session to a given device.
Remote terminal from the Mender UI
You can easily open a terminal to a device through the Mender UI in the Device details, as shown below.
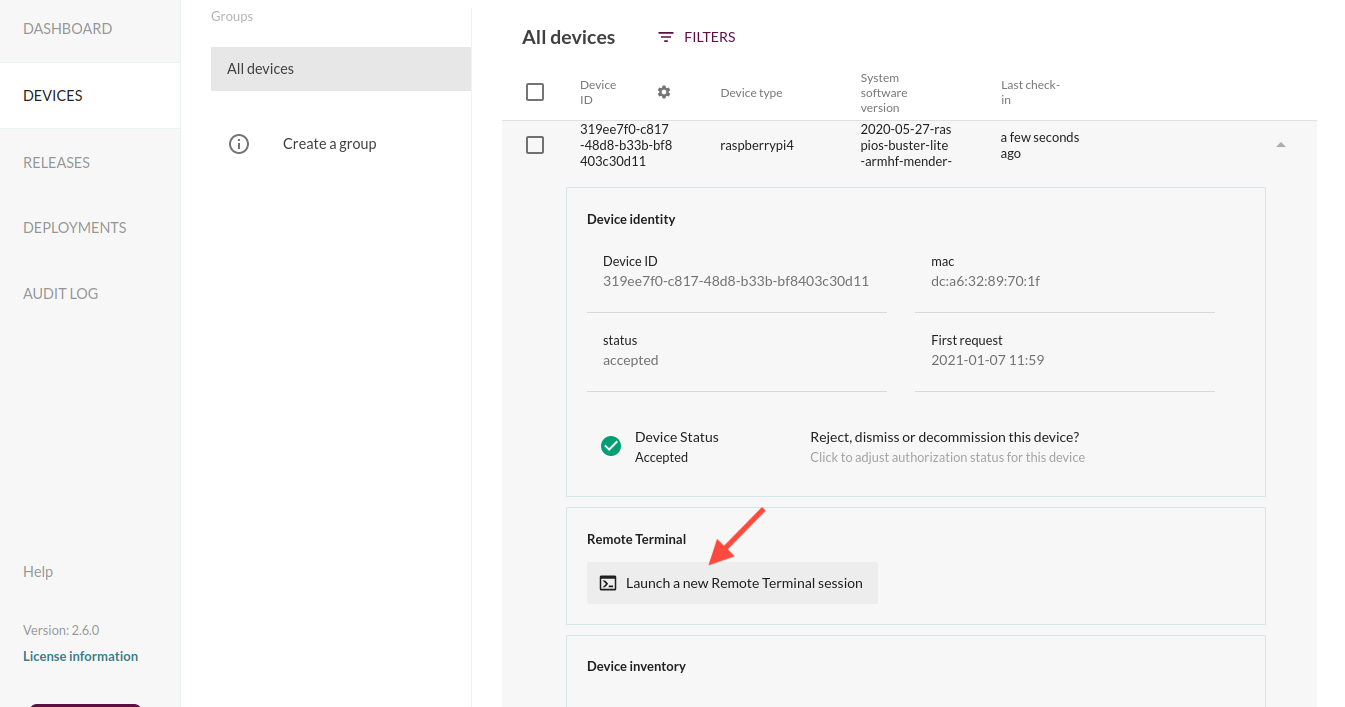
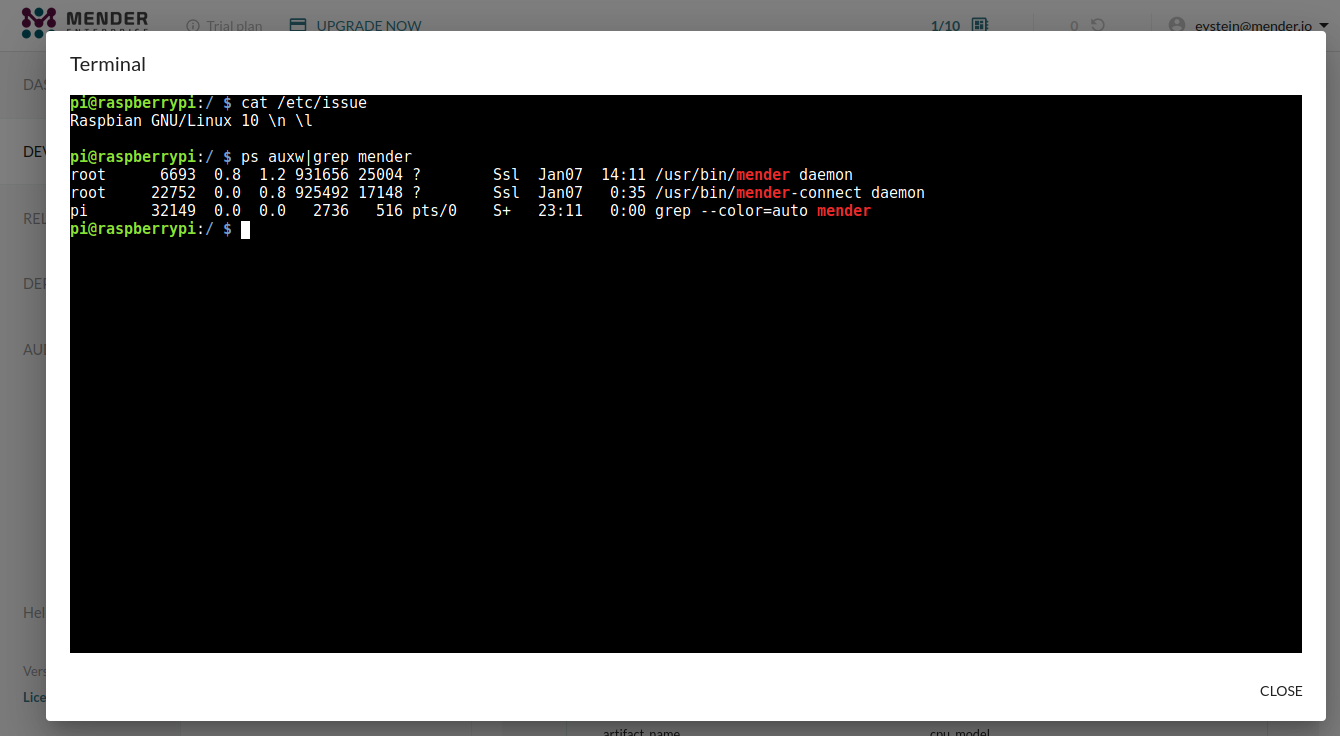
This will open a terminal aligned with the size of your browser window.
Remote terminal from your local terminal
With the new version of mender-cli,you can also access your device terminal from your local workstation terminal as well, by first obtaining the Device ID of the desired device as shown in the UI under Devices. Simply find the device in the UI, expand it and copy it to the clipboard as shown below.
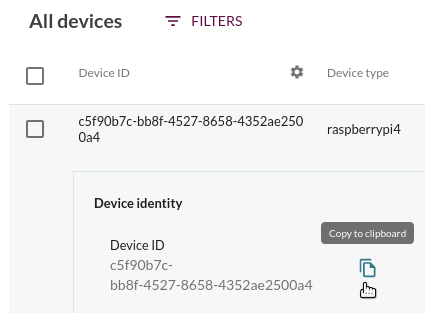
You then simply issue a command like the following:
user@laptop:~$ mender-cli terminal 319ee7f0-c817-48d8-b33b-bf8403c30d11
Configuration file not found. Continuing.
Connecting to the remote terminal of the device 319ee7f0-c817-48d8-b33b-bf8403c30d11...
Press CTRL+] to quit the session
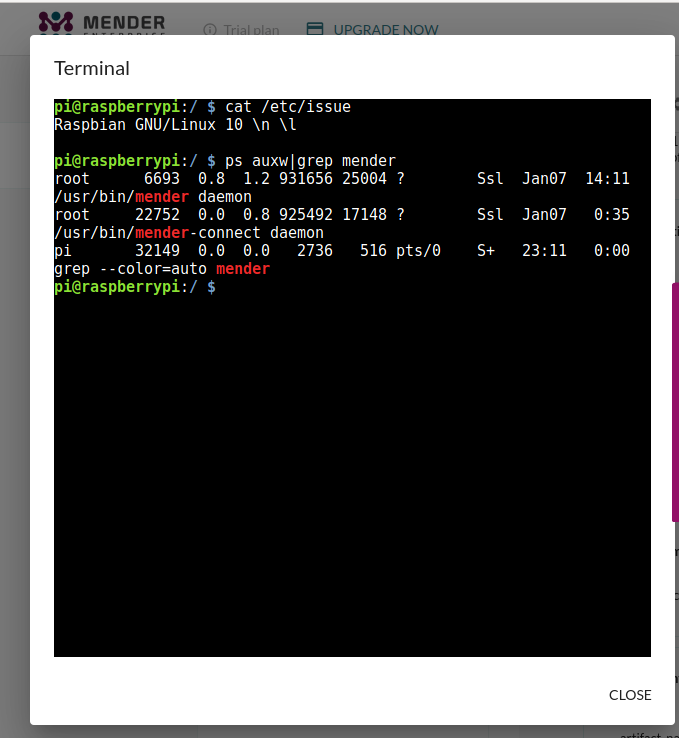
pi@raspberrypi:/ $ cat /etc/issue
Raspbian GNU/Linux 10 \n \l
pi@raspberrypi:/ $Security
The first concern with enabling a remote terminal is usually security, especially for products where privacy and compliance is important. Can anyone now do anything to any device, and nobody would know? Can this “backdoor” be exploited by attackers? For homegrown solutions this could be true, however, Mender takes security seriously.
Remote terminal is an opt-in feature: it is not enabled by default (except in onboarding for testing) neither in meta-mender (Yocto Project) nor mender-convert (Debian family and other prebuilt images). See the documentation on Installation for how to enable it.
The communication is always authenticated and encrypted with TLS - using the same key material as the Mender client. No open ports are needed on the device and you can customize which local user on the device should be used (so you can restrict its local access).
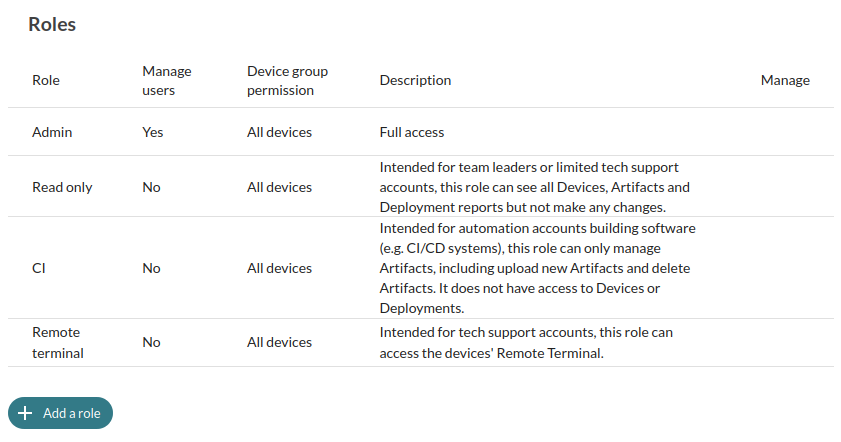
With Mender Enterprise you also gain access to Role Based Access Control (RBAC), so you can restrict which Roles (Mender server user groups) can use the Remote terminal, as seen below.
Mender Enterprise now also contains an Audit log (more on this below), and you can see which user created a Remote terminal session to which device and when in the Audit log as well.
Read more about the security of the remote terminal in its documentation section about Security.
Customizability
Remote terminal is designed to be customizable to integrate well with your environment. Aside from being an opt-in (not installed by default) feature, you can also customize it.
The terminal shell run on the device is a local shell, by default /bin/bash, so it is a full shell with your device’s environment available. You can also choose to use a different shell in the configuration if you like.
You can also configure which local device user the shell will be run as, e.g. to restrict the local access or make a specific environment available.
Resizing of the terminal window is also respected, so if you resize your browser with the Mender UI or your terminal with mender-cli, the Remote terminal will also resize to fit your screen.
There are more fine-grained configurations you can make to customize your terminal, including timeouts. Read more in Remote terminal’s Configuration documentation.
Available plans
The Remote terminal is available as open source in Mender Open Source, without the RBAC and Audit log support (which are features only available in Mender Enterprise).
It is also available on all hosted Mender plans (Starter, Professional, Enterprise) as a free trial until March 31st, 2021 so you can easily try it out. After this date you will have the option to opt in to use it for an additional fee and you will get notified about this in advance. If you choose not to use it, your plan and pricing remains the same as today.
New software versioning model
In the past, Mender has only been capable of reporting a single “Current software” per device. This became limited with increased use of Update Modules, as application updates have their own name and version tuples and are installed alongside the system.
With Mender 2.6, each Update Module (e.g. single-file) has a default scope, in which it stores the software version it has installed. You can also define your own scopes to align with the name of your application. It is implemented through the Provides attribute of the Mender Artifact.
For example, if you have a system OS version of raspios-2021-01-12 and a python application residing independently on the data partition you can see them as follows in the UI.
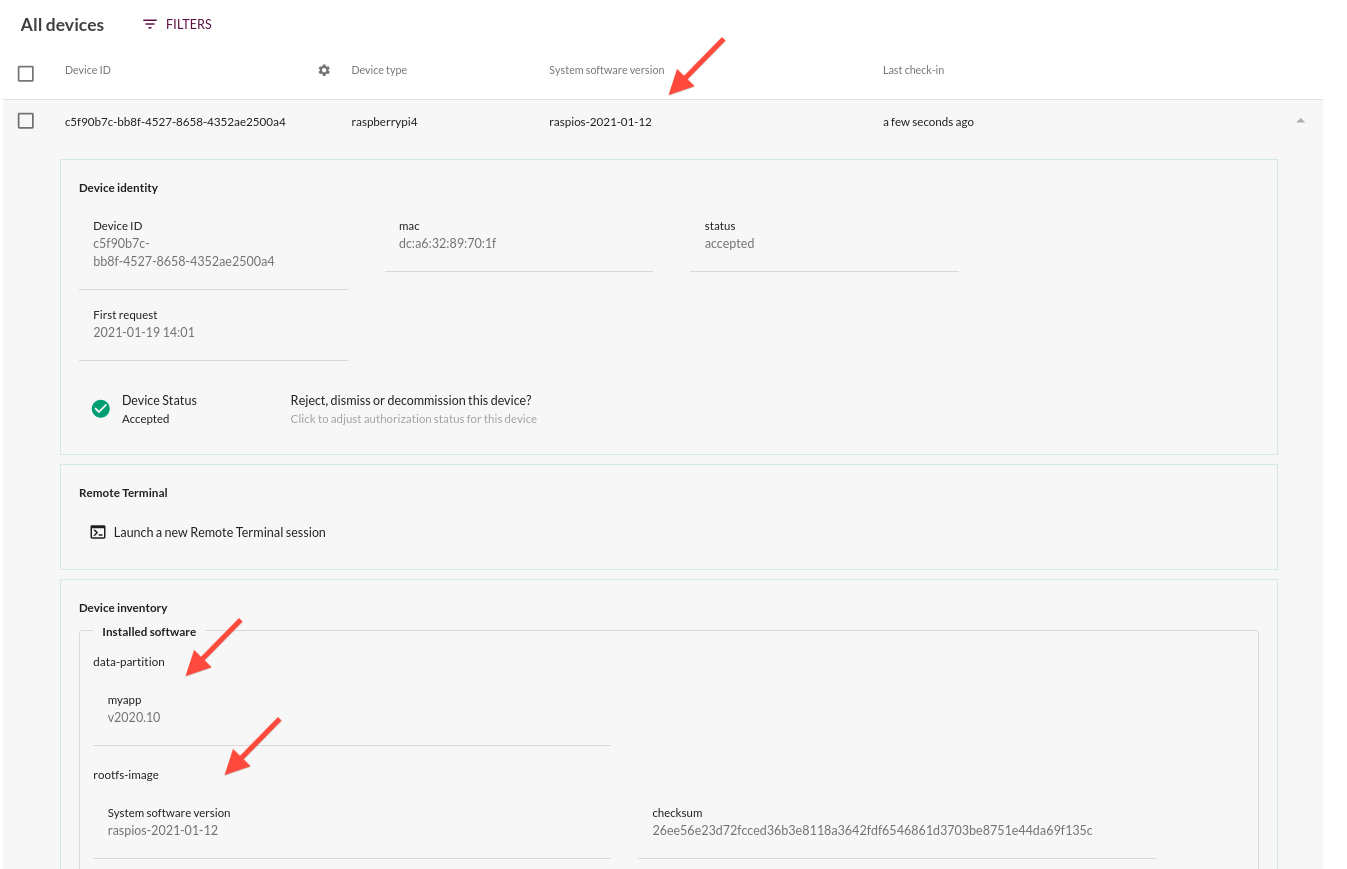
To achieve this you simply generate the system update like normal, as rootfs-image.version will be set automatically. Note that you must use mender-artifact version 3.5.0 (released with Mender 2.6.0) or later to get the required metadata support.
When you generate your application update, you need to pass at minimum --software-version to mender-artifact, but in most cases you also want to pass --software-name. The example screenshot above is generated from using the single-file Update Module generator and passing these two parameters to mender-artifact (parameters after the first -- are passed to mender-artifact unmodified):
ARTIFACT_NAME="myapp-v2020.10"
DEVICE_TYPE="raspberrypi4"
OUTPUT_PATH="myapp-v2020.10.mender"
DEST_DIR="/opt/myapps/"
FILE="myapp.py"
./single-file-artifact-gen -n ${ARTIFACT_NAME} -t ${DEVICE_TYPE} -d ${DEST_DIR} -o ${OUTPUT_PATH} ${FILE} -- \
--software-filesystem data-partition \
--software-name myapp \
--software-version v2020.10Also notice the --software-filesystem parameter which tells Mender that this application will persist across system updates because it is stored on the data partition. Read more in the new Software versioning documentation section.
This improvement is available in all Mender plans, including Open Source.
Audit logs
With the newest Mender release, we are happy to announce that Mender Enterprise on-premise now supports Audit logging! This feature has been available in hosted Mender Enterprise for a while, but Mender 2.6 brings Audit logs to Mender Enterprise on-premise users as well.
Audit logs are an important cornerstone for improving security, compliance and accountability by logging important events that can later be analyzed in case of security or operational incidents. This can greatly help in security impact analysis, as well as post mortem analysis in order to avoid similar issues happening in the future.
For example, if there is a support incident where certain devices do not operate properly, the audit log can be used to check if any recent deployments were made against them, and if so, who created the deployment and when.
The Mender Audit log creates immutable log entries when key events occur, including:
- Deployment created
- User created
- User changed (e.g. role or password)
- User removed
- Remote terminal session created and ended
In all these cases, a comprehensive set of attributes are logged such as which user performed the action, what change was, and the time. To retrieve the logs, a new user interface has been added to the Mender web UI.
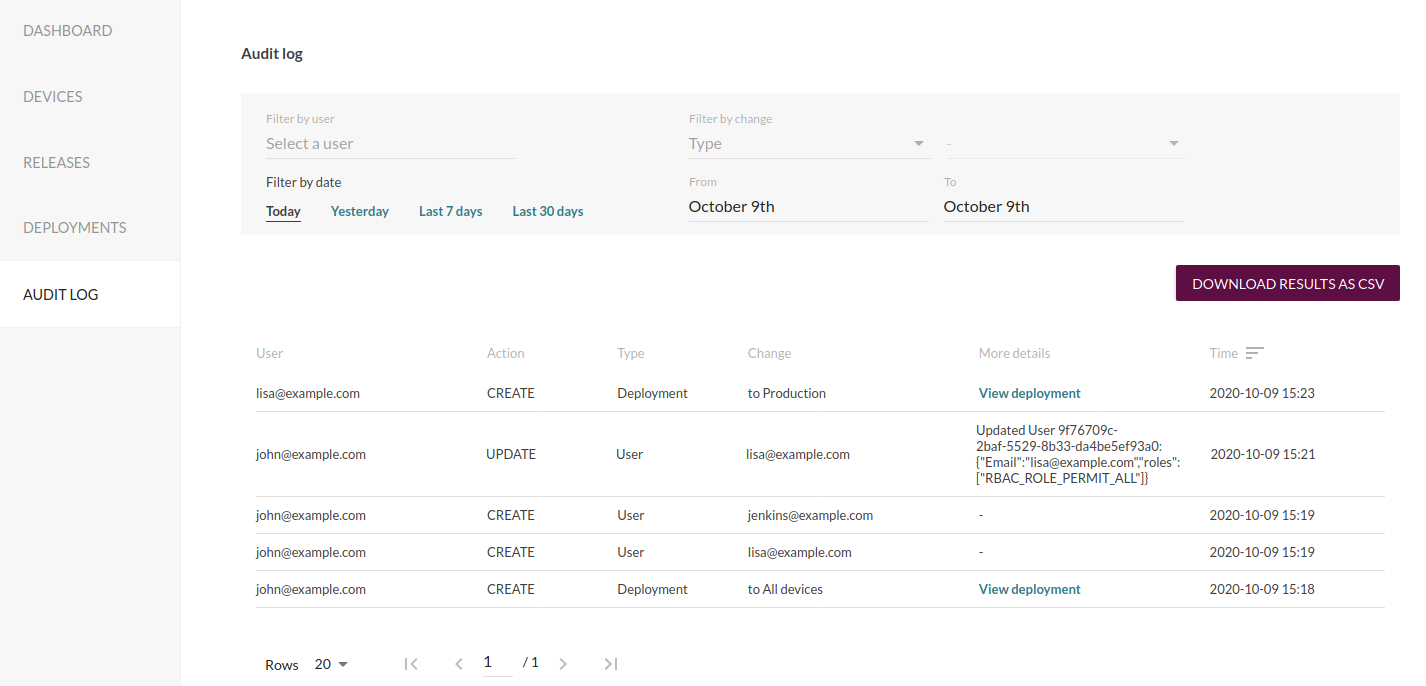
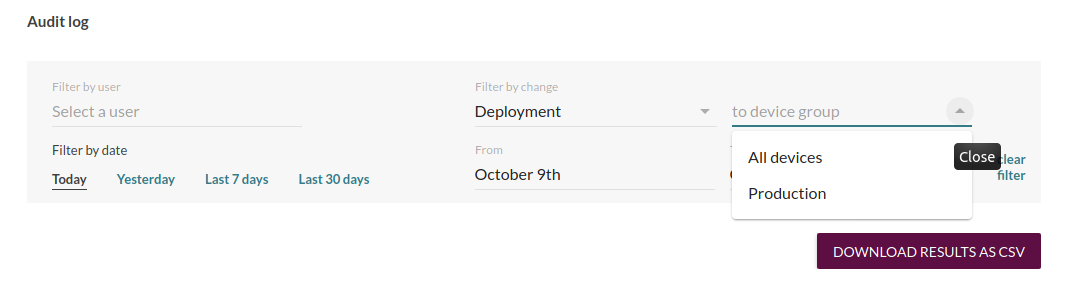
In order to inspect suspicious activity from a specific user, it supports filtering by the user performing the actions.
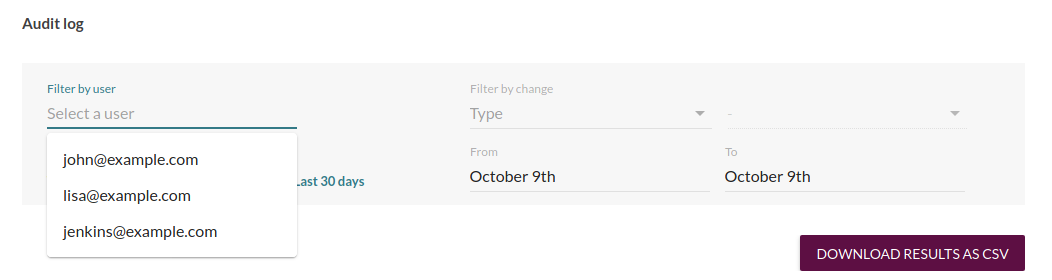
You can also filter by change type, for example to see audit log entries of all deployments to Production.
As always, all functionality is also available through the Mender REST APIs, so it is easy to integrate Mender Audit logs into other systems you have, such as collecting them into a SEIM system for correlation with other applications.
New APT repository and installation script
Since Mender now entails several components on the device, an APT repository and installation script has been added to make it easier to install and configure the components.
For now this APT repository contains the Mender device-side software such as the Mender client and the service for bidirectional communication (mender-connect). It does not (yet) contain the workstation utilities like mender-artifact or mender-cli, you can still get precompiled binaries for those at https://docs.mender.io/downloads.
Installing all Mender components (including Remote terminal) on a new running Debian family device can now be as easy as:
curl -sSL https://get.mender.io | sudo bashNote however that we recommend you use a Board integration for production devices to ensure you can deploy robust full system updates.
Deprecation of old clients using on-premise
Mender 2.6 will be the last on-premise release series to support Mender clients 1.7.0 and older out of the box. It will still be possible to support these clients by performing extra configuration steps, and more details about this will be posted in the announcement for the Mender 2.7 release. However, the recommendation is to upgrade the client to 1.7.1 or newer before upgrading the server to 2.7, so it is time to start planning this now.
This deprecation does not affect hosted Mender, only on-premise installations of the Mender Server.
Try the new features
Here are some pages with more information to get you started with the new features of Mender 2.6:
- Get started - The best place to do a quick test of the new release from scratch.
- Remote terminal - Overview section of the new Remote terminal.
- Install Remote terminal - Installation instructions for Remote terminal, including how to add it to existing devices under management.
- Downloads - Set up the new APT repository and get the new utilities in this release.
Support for your board
If you are getting started with OTA updates, or do not have time to integrate the Mender client with your board for robust A/B system updates, there are several resources available to you!
The Board Integrations category in Mender Hub is a community site to contribute, reuse and maintain Mender board integrations.
We are also happy to help with consulting services to enable verified Mender support for your board!
Share your feedback
We appreciate your general feedback on Mender, be it positive or need for improvement, in the Mender Hub General Discussions forum. Your continued feedback ensures Mender will meet your needs even better in the future!
If you believe you have encountered a bug, please submit your report at the Mender JIRA issue tracker.
We hope you benefit from the new features and are looking forward to hearing from you!
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.



