Wind River is one of the biggest enterprise grade Yocto-based Linux providers. In late 2019 they released their LTS19 version based on Yocto Zeus (3.0).
As Mender is also compatible with selected Yocto releases including Zeus, the integration with Wind River Linux just requires some small tweaks to make it work seamlessly. In this tutorial we will describe basic steps required to make both working together.
Set up a Wind River Linux project
For this project we will take advantage of Wind River’s Open Source version available in its GitHub repository. If you are using any paid plan, the steps should be the same, but you will likely have to use a different <repoURL> than the one described below and the credentials they gave you.
$ mkdir my-project
$ cd $_
$ git clone --branch <branchName> <repoURL> wrlinux-xFor theWind River® Linux LTS19 Open Source edition the git clone command should look like this:
$ git clone --branch WRLINUX_10_19_BASE https://github.com/WindRiver-Labs/wrlinux-x wrlinux-xSynchronizing with Wind River Linux repos
For this example, we are going to rely on the qemux86-64 BSP provided by Wind River.
$ ./wrlinux-x/setup.sh --machines qemux86-64 --distros wrlinux --accept-eula yesIf you want to list all the BSPs you have access to, you can run:
$ ./wrlinux-x/setup.sh --list-machinesYou may need to perform additional modifications based on the BSP you are using, for this QEMU example it works as follows, however you may want to get in contact with us or Wind River if you need a custom integration.
Set up the Wind River Linux SDK
First, we will need to set some environment variables needed to use the bitbake utility and some additional features from Wind River by running the following commands:
$ source environment-setup-x86_64-wrlinuxsdk-linux
$ source oe-init-build-envAfter the Wind River's sdk is in place, we will need to add the Mender components.
Adding Mender resources
Please be aware that as we are using a version based on Zeus, we will use the meta-mender that was developed to be compatible with it.
$ cd ../layers
$ git clone --branch zeus git@github.com:mendersoftware/meta-mender.git
$ cd -Once all the sources are in place, add Mender layers to your bblayers.conf file.
$ bitbake-layers add-layer ../layers/meta-mender/meta-mender-core/
$ bitbake-layers add-layer ../layers/meta-mender/meta-mender-qemu/Please notice there are additional layers that were already cloned as well and you can add them to your project with the command above if they make sense for your testing.
Modifying the local.conf configuration file
As the next step, let's modify the default configuration provided by Wind River®.
First, we need to ensure that internet access is enabled as they disable it by default:
BB_NO_NETWORK ?= '0'and then, standard Mender configuration should be extended as shown below (comments are only given for clarity and do not need to be added).
MENDER_STORAGE_DEVICE = "/dev/sda"
# MENDER_GRUB_STORAGE_DEVICE = "hd0"
# Lets increase the total storage as the core-image-base target is quite
# common and is the only image type that fully supports target device hardware.
MENDER_STORAGE_TOTAL_SIZE_MB_DEFAULT = "4096"Then we need to add the Mender specific configuration:
MENDER_ARTIFACT_NAME = "release-1"
INHERIT += "mender-full"
ARTIFACTIMG_FSTYPE = "ext4"
MENDER_SERVER_URL = "https://hosted.mender.io"
MENDER_TENANT_TOKEN = "<Your tenant token here>"
# Let's install the 3.1.0 version
PREFERRED_VERSION_mender-client = "3.1.0"If you are configuring a demo environment, you may want to add quick polling intervals as follows:
MENDER_UPDATE_POLL_INTERVAL_SECONDS = "5"
MENDER_INVENTORY_POLL_INTERVAL_SECONDS = "30"For more information, please visit the polling intervals section from our documentation. For additional configuration options, please refer to the variables section from our documentation.
Wind River® Linux makes usage of the PNWHITELIST flag as mechanism to avoid third party applications not validated or tested on their side to be included in a project without being explicitly whitelisted before, as described in their official docs, it requires to be formatted in the way PNWHITELIST_layerName = "recipeName1 recipeName2". So we need to whitelist some mender recipes and their dependencies by adding the following lines into your local.conf file.
PNWHITELIST_mender += 'go'
PNWHITELIST_mender += 'go-cross-core2-64'
PNWHITELIST_mender += 'go-runtime'
PNWHITELIST_mender += 'lsb-ld'
PNWHITELIST_mender += 'mender-client'
PNWHITELIST_mender += 'mender-connect'
PNWHITELIST_mender += 'mender-artifact'
PNWHITELIST_mender += 'mender-artifact-info'
PNWHITELIST_mender += 'grub-mender-grubenv'Building the wrlinux-image-core image
At this point we are ready to build our image. Just run
$ bitbake wrlinux-image-corefor building the wrlinux-image-core image. You will have access to the following images as well out of the box:
- Common Wind River images are:
- wrlinux-image-small (suggests distro: wrlinux and feature/busybox)
- wrlinux-image-core (suggests distro: wrlinux)
- wrlinux-image-std (suggests distro: wrlinux)
- wrlinux-image-std-sato (requires distro: wrlinux-graphics)
- Common Yocto Project images, typically built with distro poky, are:
- core-image-minimal
- core-image-base
- core-image-sato
After a successful build the artifacts should be available at build/tmp-glibc/deploy/images/qemux86-64.
The wrlinux-image-core-qemux86-64.mender is a symbolic link to the mender artifact you can upload to the Mender server for deploying it to the devices in the field, while the wrlinux-image-core-qemux86-64.uefiimg is the symlink that points to the raw disk file that you can use for booting up your new QEMU machine.
Running your new QEMU image
In order to run your image you should simply run a command like the following one:
$ qemu-system-x86_64 -enable-kvm -m 512 -smp 2 -bios /usr/share/ovmf/x64/OVMF_CODE.fd -drive format=raw,file=build/tmp-glibc/deploy/images/qemux86-64/wrlinux-image-core-qemux86-64.uefiimgWhere -m means memory in Mb, -smp how many cores we want to give to our guest system and -drive is used to point to the image we created that we are going to use as a disk. Additionally -bios set the filename for the BIOS and -enable-kvm enables KVM full virtualization support.
Please note the OVMF_CODE.fd file could be located in another place or even have a different name, meaning you could run $find /usr/ -name OVMF_CODE.fd or check the description of the package.
Also notice you can also run runqemu qemux86-64 if you want to use the default values.
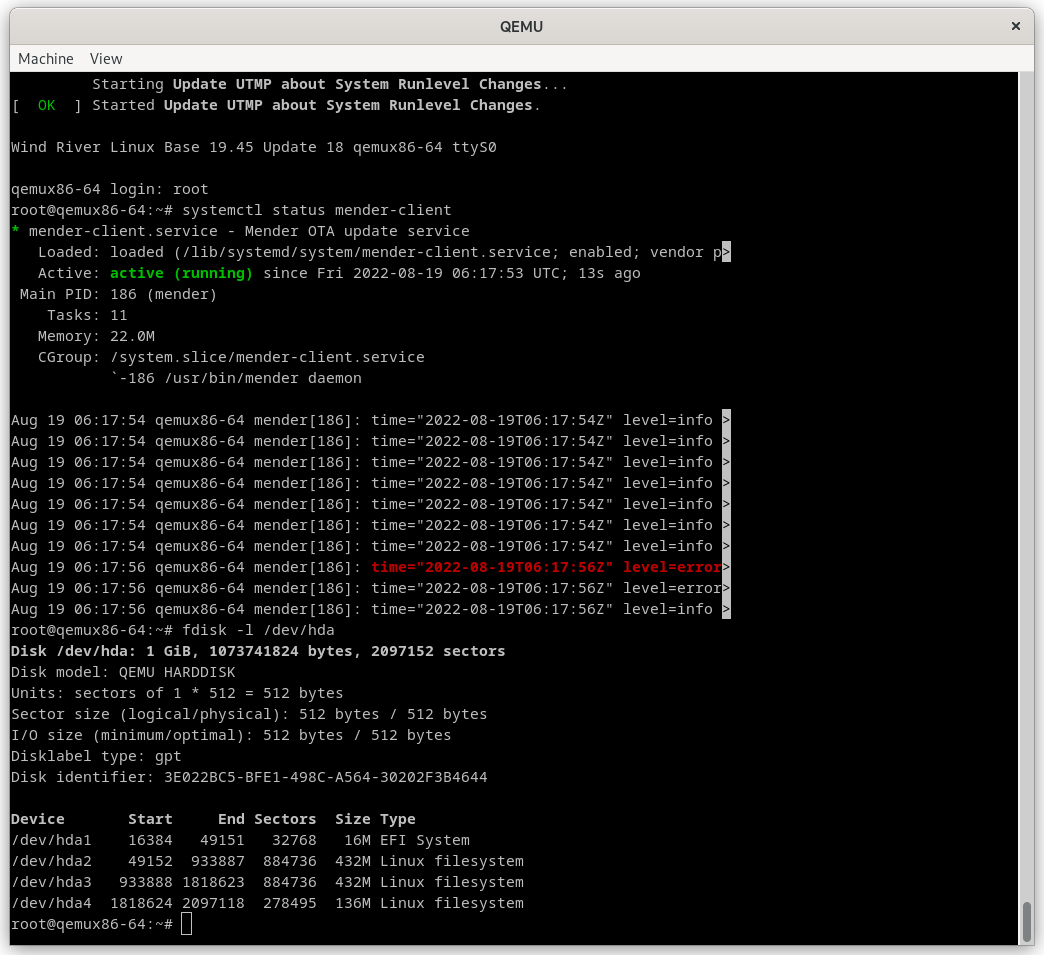
In the following screenshot, please notice:
- The banner of the system proves we are running Wind River® Linux Base 19
- The mender service is enabled and running
- The disk is partitioned as shown with the
fdiskutility.
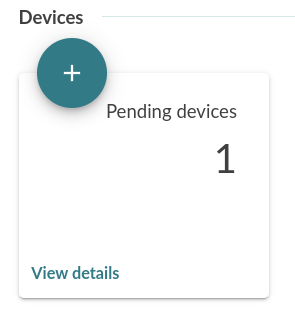
Also you can open the Mender Web UI and see there is a new device trying to be part of your fleet:
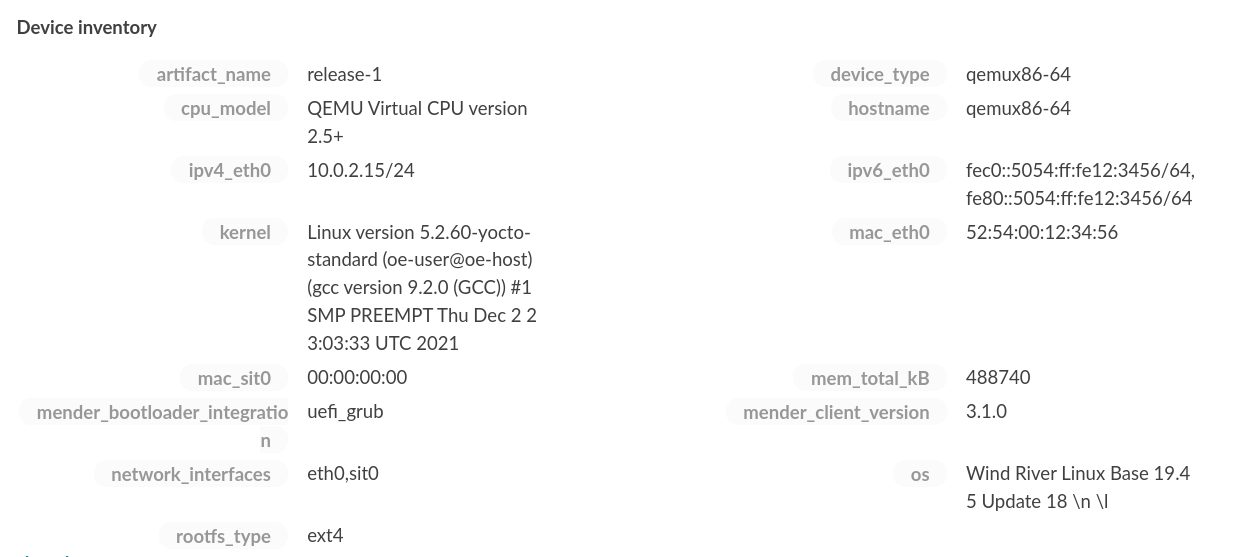
And after accepting it, then you can see its inventory data in the Mender Web UI as well:
From this point you are ready to perform secure OTA updates to your device by using Mender like with any other device by following our documentation.
I hope you liked the tutorial. You can find more tutorials inside our Mender Hub knowledge base. You should also test this easily using our free-trial account that is available for up to ten devices.
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.


