With the advent of the Internet of Things (IoT) and the proliferation of embedded connected devices across a variety of industry verticals, a host of assets are scattered globally across terrain, geography, or customer locations. Support for remote software updates is inevitable for producing customer value and effective operations. Industry verticals such as transportation, energy, consumer, smart building and manufacturing rely heavily on a potent IoT ecosystem for best possible outcomes. All software used in this ecosystem, from low-level firmware to high-level applications will need updating throughout the product lifetime.
Remote management of IoT devices scattered globally involves grouping and accessing devices, provisioning, configuring and monitoring remotely and securely from one or more central locations. In managing large fleets of connected devices, one critical challenge is the ability to efficiently deliver remote software updates over-the-air (OTA) during the product life-cycle, with minimized operational risk calling for industry best practices in security and robustness.
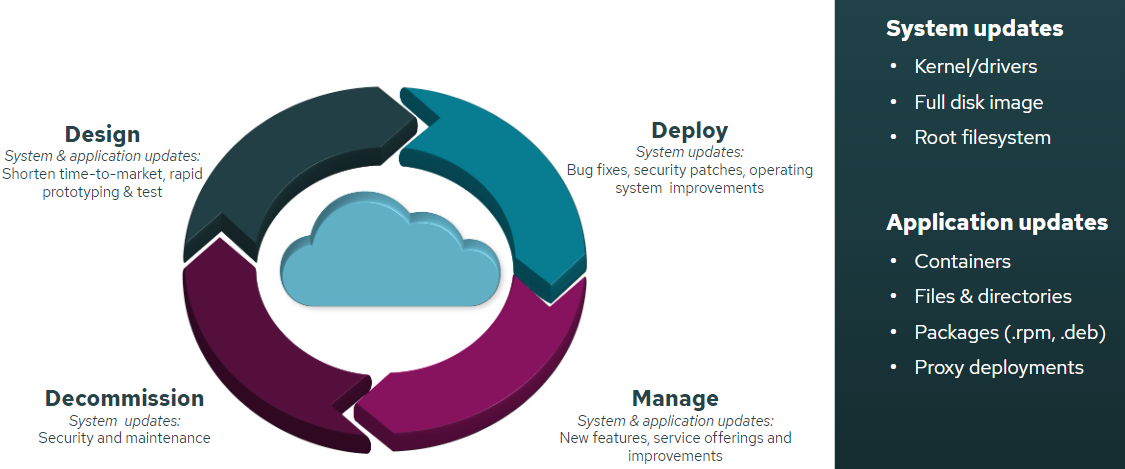
Changing needs for software updates during device lifecycle
Real-time software updates are needed to counter the bugs that come from the inevitable increase in complexity as software grows. Software patches must be delivered dynamically and systematically to IoT devices over the entirety of their life cycles.
System-level and application-level updates
Software updating requirements during a product’s lifetime vary from product to product and from industry to industry. Updating requirements can be components related to a whole system or applications. System updates can be low level bootloader, kernel, root file system that enable the underlying operating system software capabilities. Application layer updates in the higher software stack deals with user experience and device functionality and may require updating containers, packages, files, and configurations.
From pre-production to decommission
When in pre-production environments, the software updating needs arise from the desire to do rapid prototyping and testing, get faster user feedback for feature development and ultimately shorten time-to-market. As devices reach the end user there are various use-cases requiring both system and application updates, independently. For example, during the initial launch of the product in market (introduction), there may be a need for system updates to fix bugs, patch security or update the full operating system image to the latest version as much might have changed when the product sat idle in shopping shelves. Comparably, application updates may occur in the growth and maturity phases of the product when service providers and device manufacturers push new features, improvements and service offerings to increase their monetization opportunities and increase their customer’s loyalty and satisfaction.
Security considerations for software updates in an IoT device management platform
Managing IoT security threats is different from managing security threats in traditional IT security environments such as servers, laptops, desktop computers and mobile devices. Particularly in server IT, security is mainly focused on protecting data stored in large server infrastructures that are in close proximity and can be physically, or semi-physically (ILO) reachable at relatively low cost. However, in the case of IoT devices, while data protection concerns still exist they mainly extend further into the physical world and most often at large scale with heavy reliance on battery and wireless connectivity where interruption in operations can cause millions of dollars of damage within a short period of time. Therefore, it inherently becomes harder to secure IoT devices as compared to other environments.
A secure software update process can be defined as: a) the authorized device has the latest available b) authorized software, c) deployed by authorized people. The expected outcome is that the device has no adverse effect on device functionality resulting from checking, downloading and installing software files.
The end goal for hackers is to install malicious software and there are ways to prevent this from happening:
-
Unverified software deployment: The client running on the IoT device needs to have the ability to verify that the update comes from a trusted source. One way of achieving this is to sign the software using a protected private key which is stored and used on a signing system. The verification happens using the corresponding public key on the client (device). If a signature verification check passes, then the software update is considered safe.
-
Compromised build systems: You do not want your build system (source) to be compromised. Malicious software is hard to detect if it is injected at the source. It is important that your OTA system is connected through the build system using established APIs as this will reduce the chance for manual errors leading to insecurity.
-
Convoluted updates: If your OTA system is compromised, adversaries can update any device with any malicious software. It is important that your OTA solution supports 2-factor authentication and has extensive logging capabilities.
Developers and device manufacturers must address security threats when designing connected products. If implemented poorly even the smallest open backdoor from the most innocent IoT devices can expose your entire corporate network.
Recent articles
Complying with the US FDA and EU MDR requires software updates
IoT in 2026: Edge AI, growing complexity, and the demand for smarter updates
New Mender experimental AI-enabled feature
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.




