IoT Device Security: Why are Best-of-Breed OTA software update systems required?

Many organisations suffer from having fragile and insecure homegrown solutions for software updating of IoT devices. A best-of-breed OTA software update solution from a professional system management vendor is the only alternative for a robust and secure IoT device fleet and a properly protected corporate network.
Where USB sticks are used to update the devices manually, additional cost and burden is incurred when technicians have to perform the updates manually. Worse still, it increases the risk that an unauthorised user will access the device and gain entry to the whole corporate network. If the right security protections are not in place on IOT devices, hackers can get access and steal trade secrets, delete valuable company information and back ups, issue ransoms for financial gain and even remain in stealth, planting backdoors to return into the network again and again.
What are the real threats to IOT device security?
Ransomware threats can breach an enterprise. In March 2019, one of the world’s largest aluminium companies Norsk Hydro was hit by a ransomware attack. Immediately production lines stopped at its 140 plants and they had to move to manual operations. Eventually, all 35,000 employees were affected and the overall financial impact of the attack was €71million. The initial damage had occured 3 months earlier when an employee unknowingly clicked on an email attachment and allowed the hackers in to plant the ransomware. Lockergoga, the name of the malware, encrypted the files on desktops, laptops and servers throughout the company. It also posted a ransom note on the screens of the corrupted computers.
In a period where many enterprises are undergoing digital transformation, the security risk increases as software becomes more pervasive in their products. When there was little software in an enterprise’s products, there was not much damage hackers could do. This situation has changed dramatically as the software stacks have increased dramatically in size and value. In turn, the potential harm in having an insecure and fragile homegrown OTA software updater increases exponentially.
The most common security issues for IOT devices emanate from known vulnerabilities not being patched. In truth, most vulnerabilities can be addressed with patches so organisations must patch their devices. This is real security.
There are two types of vulnerabilities that hackers can exploit:
- Zero day vulnerabilities - this is where the vulnerability is not yet publicly declared
- Known vulnerabilities - these have been published on the CVE and can be easily fixed by patching software
What is the solution to these threats to IOT device security?
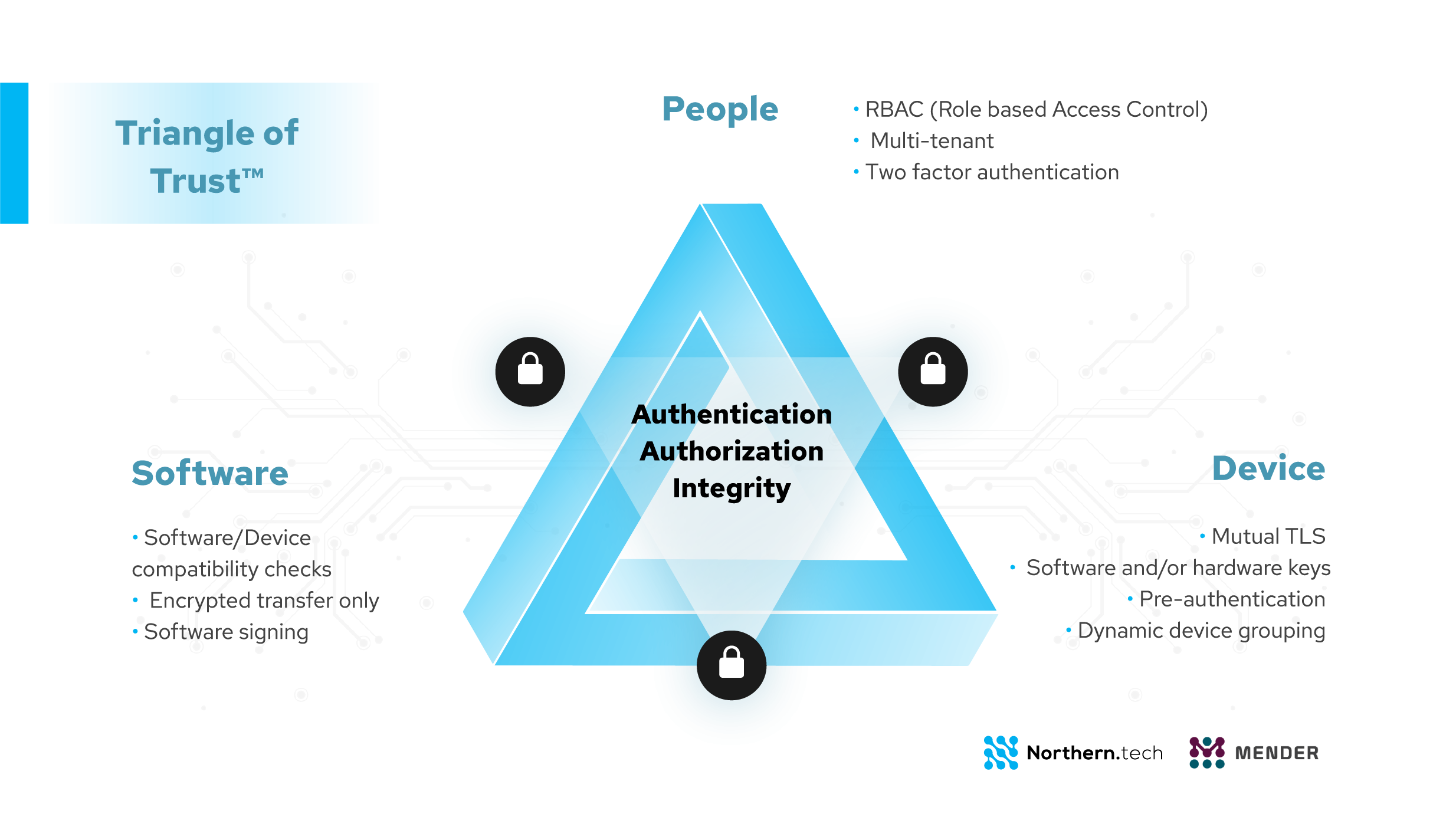
First of all, employees need to be educated on how to address challenges to the security of IOT devices and social engineering threats. Putting in place Zero trust security infrastructure that extends to the IoT infrastructure is equally important. Mender uses the Triangle of Trust™ framework in its product design to protect IOT devices and network security. Only the right people should have access to the right software on the right devices.
The solution for enterprises is to minimize the attack surface by ensuring that an updating system is in place to continually eradicate system vulnerabilities. This can be done very effectively by supplanting fragile and insecure homegrown updating systems with best-of-breed OTA software updates systems that perform full system updates and patches software.
Main ways to secure IoT devices:
- Implement a physical policy where rugged casing is applied to the IoT devices. This is to ensure if a device is stolen, it cannot be compromised.
- The second and most highly effective way is to apply a virtual policy and use software to protect the device if a hacker manages to unmount an IoT device. With a connected device, you need to prevent a hacker from being able to tamper with, or re-engineer the device.
An enterprise should ensure that the software on the device is encrypted, and that it has as few moving pieces (dependencies) as possible. Better still is to implement a read only system on the device so the only way the device can be updated is to get a whole new blob through an OTA software update. The benefit is that no configuration is required as everything is encrypted. The only way to make changes to the device is to make a full OTA update to it.
With homegrown comes the increased threat of bricking
There is another risk with homegrown updating solutions: In a system that is locked down, a fragile and insecure homegrown updating system might brick the device. If the update were to fail, there might not be an engineer available to fix it and in the worst case scenario, the device might have to be shipped back to the factory for a hard reset. So where you have locked down security policy, Mender is the preferred option. It provides a secure and stable solution and has an A/B partition to roll back to the previous update in cases where the update fails preventing bricking.
For devices that are connected to the Internet, the number one way to update these devices is still by USB sticks. Very few new IoT devices will support USB but you will still see some product categories such as Burglar Alarms that will use them. Increasingly products are connected to the Internet and so a robust system for OTA updates is the best way to keep them secure. USBs both add extra costs to the hardware and increase the attack surface. The industry will soon stop using USB sticks al together. Large enterprises will have both on-premise installations and public cloud installations and this hybrid model will be used for the foreseeable future - for at least the next 10 years. A software updating policy and OTA update solution that supports both OTA and offline updates is a mandatory requirement.
Basic device hardening
Organisations should also apply basic device hardening policies. Such policies might address issues like:
Hard coding a password Using the same username and password across all devices Using clear text to store sensitive configuration information such as URLs to back end databases Unencrypted data transfers between device and other connected services
Botnets and DDOS
Botnets are distributed services that exploit known vulnerabilities or basic application security issues - password, access a printer through an exposed port. Botnets are not the biggest threat. Of greater concern is a possibility of DDOS attacks where the main infrastructure could be compromised. Devices are connected to a gateway and if this gateway is being exploited then bad things can happen to the IoT devices. Your devices could be exposed and they provide entrance points into the enterprise infrastructure.
Invest in best-of-breed over homegrown
In summary, a best-of-breed OTA software updating solution will ensure that IoT devices are kept properly up-to-date with the latest security patches whilst ensuring that the devices will not brick in the event of a failed update. These are two things that are very difficult to achieve at scale with a homegrown method of updating. As software continues to constitute an ever increasing part of the overall value of a product, so should the urgency moving away from manual and home grown systems to something stable and secure provided by professional system management vendors.
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.


