We are happy to announce the production releases Mender 1.6.0 and 1.5.1!
The ongoing focus for Mender is to:
- broaden the supported device types
- make the device integration process as easy as possible
The key features of Mender 1.6 are covered below, and you can see the detailed items in the release notes of Mender 1.6.0 and Mender 1.5.1.
Some of the features below are part of meta-mender's sumo branch, strictly speaking not Mender 1.6. If you are using Mender 1.6 with meta-mender sumo, all these features are available. Otherwise, please see the Mender 1.6.0 release notes for more information on where a given feature is implemented.
Automatic integration for most ARM-based devices
In order to support atomic updates with rollback capability, Mender requires integration into the boot process of devices. Mender users have reported this to be the key obstacle to get started with Mender, so Mender developers have been working hard to make this easier. Mender 1.6 improves this in several ways, as you can see in the following sections.
The most important improvement is that no board bootloader integration is required for most ARM-based devices; this can now be done automatically in run-time! This feature is using GRUB as an intermediate bootloader to do the partition selection and UEFI emulation in U-Boot to load GRUB.
Note that this feature is not yet enabled by default, but it will be the default from meta-mender branch thud (2.6). To enable it in sumo, add the following configuration in your local.conf:
MENDER_FEATURES_ENABLE_append = " mender-grub mender-image-uefi"
MENDER_FEATURES_DISABLE_append = " mender-uboot mender-image-sd"See the documentation on integrating with GRUB for more information.
However, this will most notably not be enabled on raw flash-based devices (NAND/NOR) as GRUB does not support raw flash. The next section will show how integration with raw flash devices is made easier by a different feature.
Autopatching for raw flash devices
To simplify the integration process for devices based on raw flash (and thus not covered by the run-time integration above), a tool to automate the integration patch generation that was released in December 2017 has been extended. In its initial release back then, the autopatching tool supported only block-based storage.
We are happy to announce that with Mender 1.6, automatic patch generation is also supported for raw (i.e. NAND/NOR) flash devices! Take a look in the updated documentation on raw flash for an introduction on how to get started. For a comparison, you can see how many fewer steps this is than supporting raw flash in Mender 1.5!
x86 BIOS support
Mender 1.5 introduced support for x86 devices through the UEFI framework.
In Mender 1.6 this functionality is extended; Mender 1.6 also supports BIOS-based x86 devices! Take a look at the documentation on GRUB support for steps to integrate Mender with BIOS-based x86 devices.
Yocto Project sumo (2.5) support
meta-mender has a brand new sumo branch, so you can integrate Mender with this newest stable release of the Yocto Project!
mender -check-update
When testing and diagnosing and you have shell access to a device, it is often useful to kick off an update immediately rather than waiting for the next scheduled update check by the Mender client daemon.
This is now supported by running mender -check-update on the device. This command will communicate with a running Mender client daemon and tell it to check for a new update with the Mender server immediately.
Note that this functionality is only applicable when running Mender in managed mode; if you are running Mender in standalone mode you are already triggering the update process from the shell or a script.
Custom device identity attribute
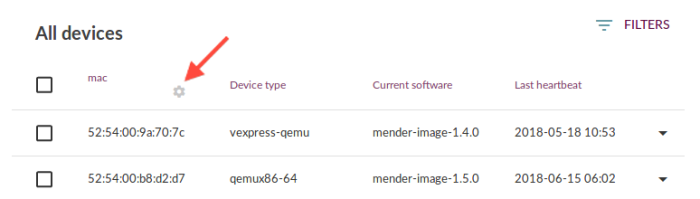
You can now select which of your device identity attributes you want to use in the Mender UI. For example, you could use the mac address, hostname or any other attributes you have as part of your device identity scheme. This helps you recognize the devices more easily, both in the Devices tab, and in Deployments.
To configure which device identity attribute to use, simply click the gear icon at the top of the ID column under Devices. You can also set it from Global settings. In order to avoid confusion, this configuration is global and affects all users of your Mender server (for on-premise Mender) or organization (for Hosted Mender).
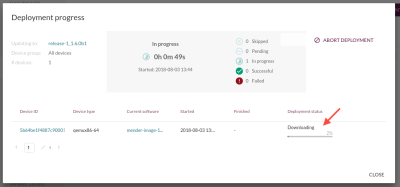
Deployment progress bar
When doing deployments, the deployment progress bar for each device will now move forward continuously as your deployment is in progress.
Easily modify image configuration
It is often convenient to do small modifications of images with Mender integrated, such as changing the server URL, certificate or polling interval.
In Mender 1.6, mender-artifact has been extended to allow reading from and writing to any file within the root file system, using the options cat, cp or install (to also set permissions). They behave similarly to the familiar Unix tools, but work on Mender Artifacts and disk images.
For example, to show a configuration file inside a Mender Artifact, simply run:
mender-artifact cat artifact.mender:/etc/hostsAs another example, update the Mender configuration inside an Artifact by running the following command:
mender-artifact cp /tmp/mender.conf artifact.mender:/etc/mender/mender.confFore more examples, please head over to the documentation on Modifying a Mender Artifact.
WiFi support in Raspberry Pi 3 demo images
WiFi is now enabled in Raspberry Pi 3 demo images (BeagleBone Black does not have a WiFi module onboard).
In order to test the new demo images, follow the documentation tutorial for on-premise Mender or the Help section in Hosted Mender.
Please note that in general you can use any network interface (e.g. Ethernet, WiFi) to connect to a Mender server, the new WiFi support is part of the demo images used for initial testing of Mender.
Try Mender 1.6
The documentation has a new 1.6 section that includes all the resources you need to get going. To test the new features, you can start with these pages:
- Install a Mender 1.6 demo server
- Automate integration using GRUB for ARM and x86
- Use autopatching for integrating raw flash devices
- Build a Mender 1.6 Yocto Project image
- Modifying a Mender Artifact
- Preauthorize devices
Upgrading to Mender 1.6
If you are using Mender 1.5, follow the Mender 1.6 upgrade documentation to upgrade to Mender 1.6.0.
It will likely work to use the same document to upgrade older releases of Mender as well, but please note that the official and tested upgrade path is always from the previous minor or patch release (i.e. 1.5.x releases for 1.6.0).
Sign up for Hosted Mender
Hosted Mender is a secure Mender server we host for you, so you do not have to spend time maintaining scalability, security, certificates, uptime, upgrades and compatibility of the Mender server. Simply point your Mender clients to our server! It is inexpensive and priced very competitively with the cost of self-hosting a Mender server.
Hosted Mender is already updated and fully compatible with the new Mender 1.6 client releases.
Sign up and get your $120 free credit for Hosted Mender today.
Support for your board
If you are getting started with OTA updates or do not have time to verify the Mender client works with your board, we are happy to help with professional services!
Share your feedback
We are happy to continue to see your general feedback on Mender, be it positive or need for improvement, on the Mender mailing list. Your continued feedback ensures Mender will meet your needs even better in the future!
If you believe you have encoutered a bug, please submit your report at the Mender JIRA issue tracker.
We hope you enjoy the new features and are looking forward to hearing from you!
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.