As always, security and robustness is the prime directive of Mender and yet this new release for hosted Mender is another testament to that directive.
We are happy to announce that Mender Enterprise now supports Audit logging!
Audit logs are an important cornerstone for improving security, compliance and accountability by logging important events that can later be analyzed in case of security or operational incidents. This can greatly help in security impact analysis, as well as post mortem analysis in order to avoid similar issues happening in the future.
For example, if there is a support incident where certain devices do not operate properly, the audit log can be used to check if any recent deployments were made against them, and if so, who created the deployment and when.
The Mender Audit log creates immutable log entries when key events occur, including:
- Deployment created
- User created
- User changed (e.g. role or password)
- User removed
In all these cases, a comprehensive set of attributes are logged such as which user performed the action, what change was, and the time. To retrieve the logs, a new user interface has been added to the Mender web UI.
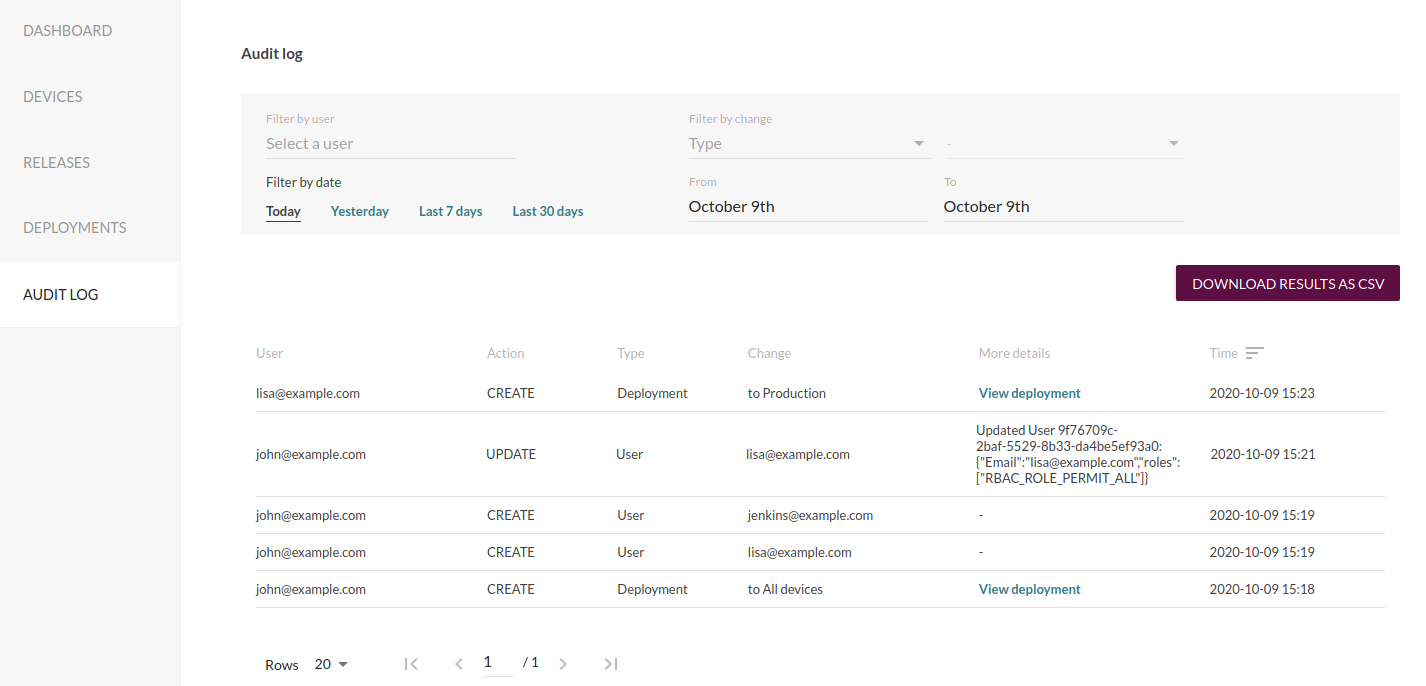
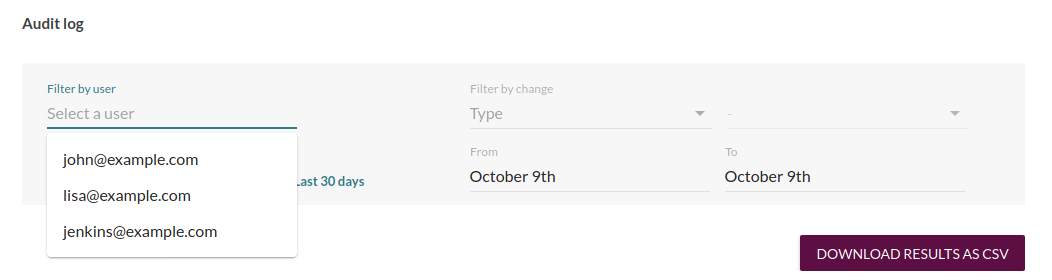
In order to inspect suspicious activity from a specific user, it supports filtering by the user performing the actions.
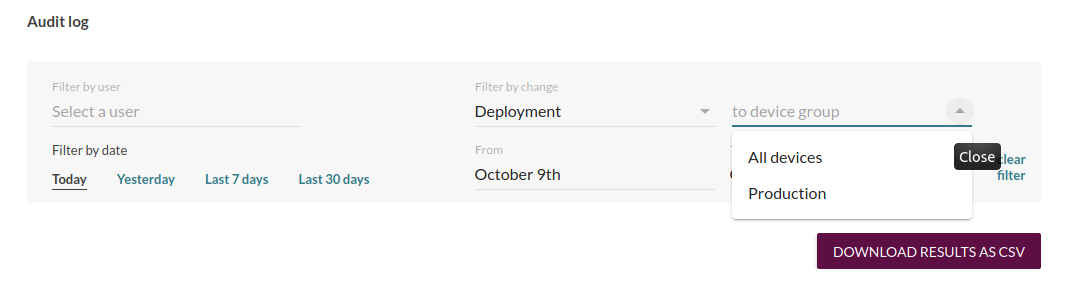
You can also filter by change type, for example to see audit log entries of all deployments to Production.
As always, all functionality is also available through the Mender REST APIs, so it is easy to integrate Mender Audit logs into other systems you have, such as collecting them into a SEIM system for correlation with other applications.
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.



