Personal Access Tokens simplify the API-based integration with Hosted Mender
It is now possible to generate and use Personal Access Tokens on Hosted Mender when performing management API calls.
Before the introduction of this feature, the only way to obtain a JWT token to perform API calls was using the log-in end-point. However, the token returned lasts one week only. Therefore, storing and reusing it, for example, from a CI/CD pipeline or a scheduled job, is not practical.
Personal Access Tokens are long-lived JWT tokens that you can use to programmatically access the Mender management APIs without logging in each time you need to perform API calls or handling the JWT token expiration.
Personal Access Tokens act as API keys you can use from your CI/CD pipelines or scheduled jobs to access the Mender management APIs. The Personal Access Tokens impersonate the user who generated them, including all the permissions and roles associated with the user.
You can generate a Personal Access Token using the web-based UI from the "My profile":
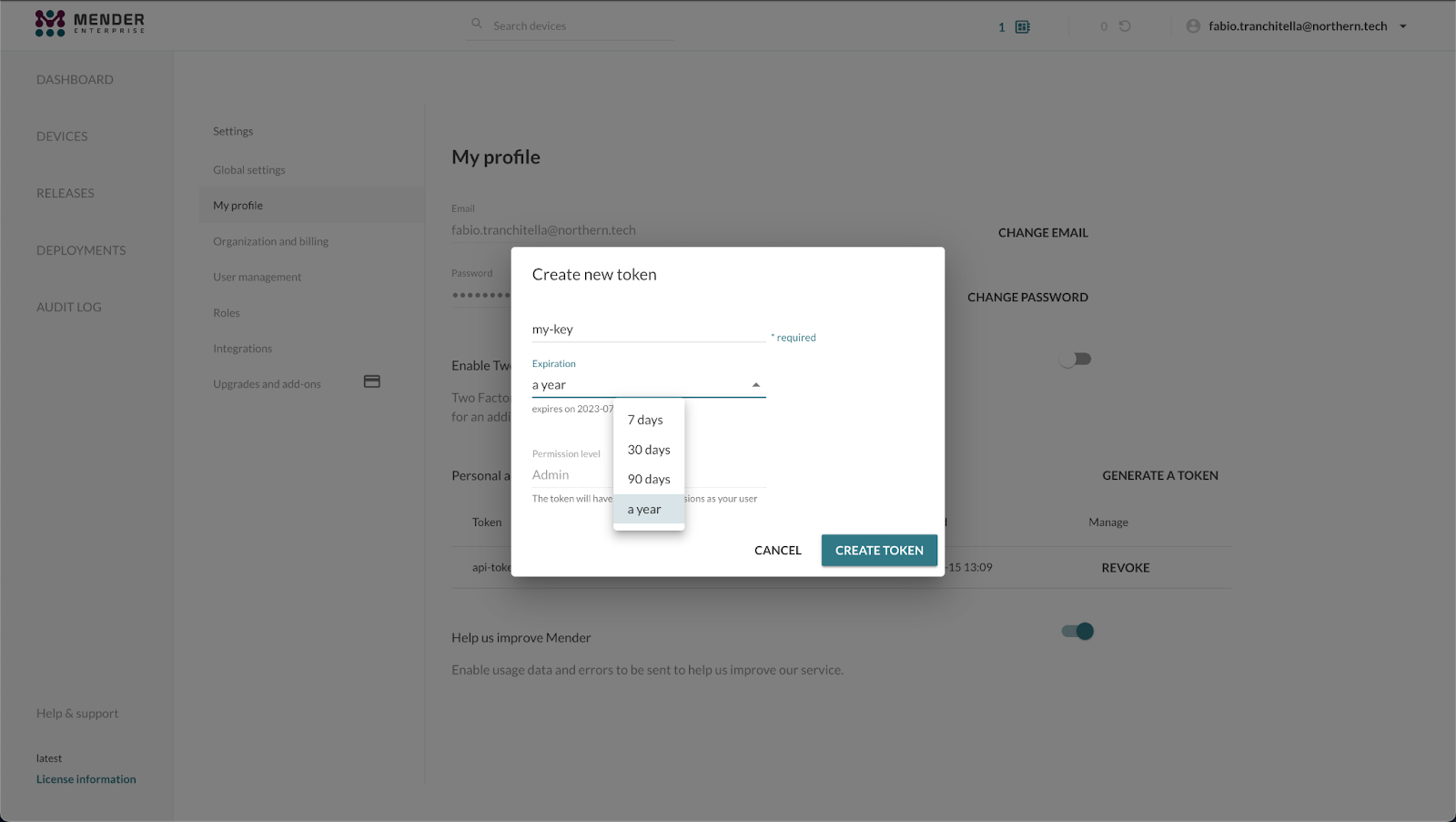
You can specify a descriptive name for your token and an expiration time ranging from one week to one year. In the same view, you can also list and, eventually, revoke your tokens:
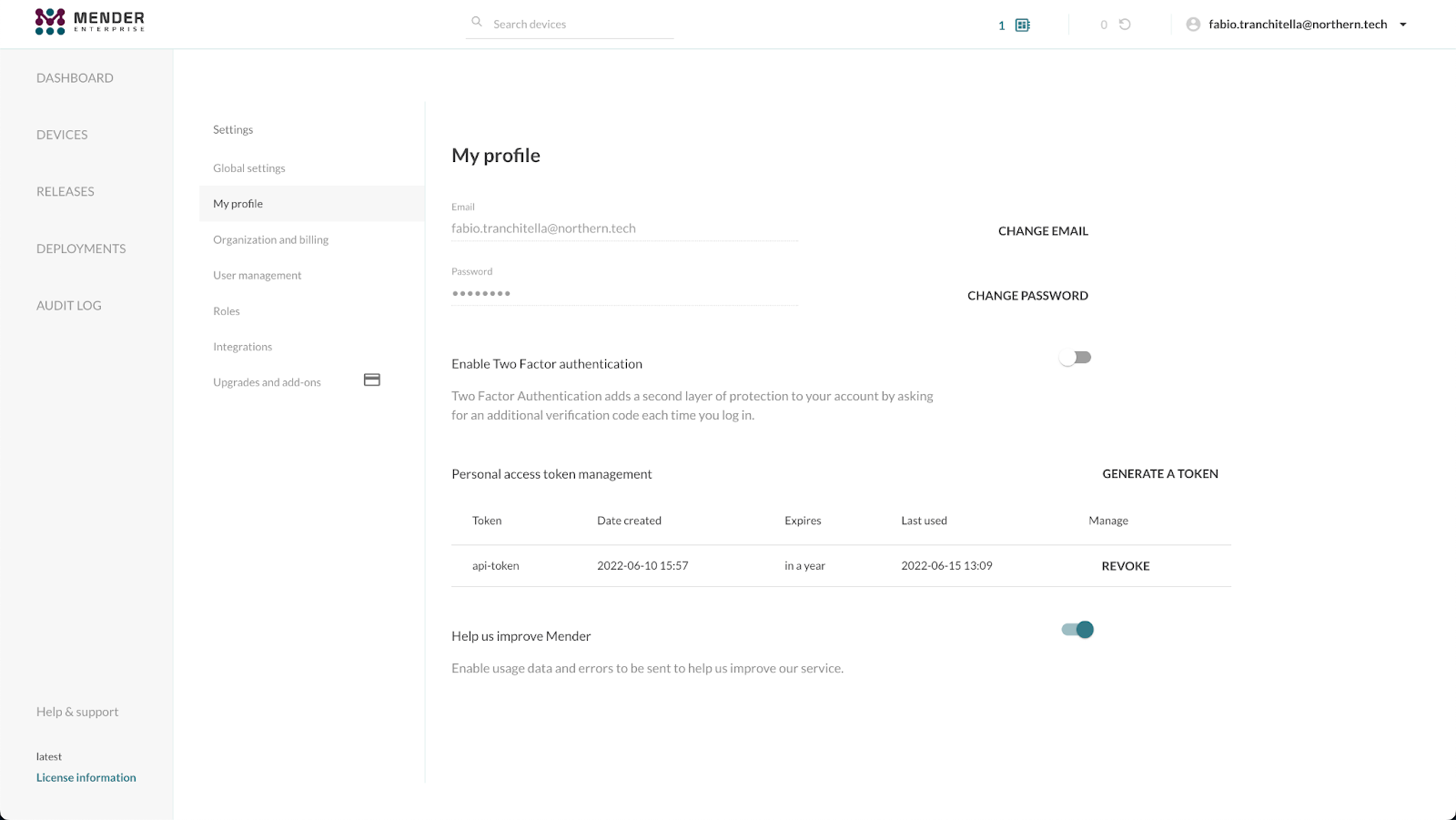
In our documentation, you can read more about using the management APIs, including the Personal Access Tokens.
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.


