At Embedded World 2025, Joël Guittet, Project Manager and Developer at The Embedded Kit and Josef Holzmayr, Developer Enablement Expert at Mender, broke down the intricacies of A/B partitioning, sharing real-world insights and best practices to help developers navigate firmware update challenges. Throughout the event, one recurring theme emerged in conversations with industry experts: fragmentation in the embedded ecosystem continues to create inefficiencies, increase maintenance burdens, and slow progress in deploying secure firmware updates.
Fragmentation in the embedded ecosystem is often driven by the decision to build firmware update systems in-house. While homegrown systems are typically tailored to specific product needs, their core functionality tends to mirror implementations across the industry. As products scale and grow in complexity, managing and maintaining these homegrown systems becomes increasingly difficult. Industry experts pointed out that developers often “reinvent the wheel,” not necessarily because they should, but because they can. The upcoming 2025: The State of Industrial IoT Device Lifecycle Management report reinforces this sentiment, showing that 46% of OEMs prefer to build infrastructure internally if in-house talent is available, even when third-party solutions exist.
While internal development may seem like a practical choice, as Holzmayr emphasizes, it often results in complexity and hidden costs. In the same vein, he references a notable Jeff Bezos principle: “Whoever makes your electricity has no impact on how your beer tastes.” In other words, just because you can build something in-house doesn’t mean it’s worth the investment, especially if it doesn’t contribute to your competitive edge.
So, what does this mean for the future of embedded systems? It highlights a strategic shift: Instead of allocating engineering resources to maintain an infrastructure that doesn’t drive product differentiation, more teams are turning to standardized, proven solutions that accelerate time-to-market and reduce technical debt. In doing so, OEMs overcome the numerous challenges fragmentation poses, such as duplicated effort, inconsistent processes, and high long-term maintenance costs.
The shift towards standardization also supports a broader goal: building systems that are more adaptable, secure and resilient-especially as software plays an increasingly central role in product functionality and competitiveness.
The importance of firmware and software updates
Whether you're building an EV charger, a medical device, or any other connected product, devices require regular firmware and software updates to:
- Fix bugs and improve reliability
- Optimize performance, including reducing boot time
- Introduce new features to enhance the user experience
Regulations like the European Union Cyber Resilience Act (EU CRA) and the Radio Equipment Directive (RED) also mandate that vulnerabilities be addressed and updates be applied throughout a product’s lifecycle.
Supporting these capabilities is essential to maintain long-term security, efficiency, and compliance, especially in regulated environments.
However, implementing a robust, fail-safe update mechanism isn’t easy—especially when organizations rely on fragmented or homegrown solutions. Without standardization and built-in safety measures, these systems are often difficult to maintain and increase the risk of update failures across large device fleets. This reinforces the need for structured OTA strategies that prioritize reliability, stability (such as rollback capabilities), and maintainability. One widely-adopted OTA update approach uses dual partitions to isolate the update process, reducing risk and ensuring devices are available even if something goes wrong.
A/B Partitions: A robust OTA strategy
In the early days of embedded systems development, firmware updates were often handled by manually copying files using shell scripts — a process that was error-prone and difficult to manage at scale. Failures were common, and there was little in the way of rollback or recovery mechanisms. To improve reliability and safety, the use of A/B partitions (also known as active/inactive partitions) emerged as a structured approach for implementing fail-safe OTA updates.
How A/B partitioning works:
- The system runs on the active (A) partition while an update is written to the inactive (B) partition.
- If the update succeeds, the bootloader flips to boot from the B partition.
- If something goes wrong, the system rolls back to the A partition, ensuring the device remains operational..
A key point for security is that persistent data should never be stored on the root file system (rootFS). Since the root file system is replaced during an update, any data stored there will be lost. Instead, use dedicated partitions for logs, configuration files, and application data to ensure critical information remains intact across updates.
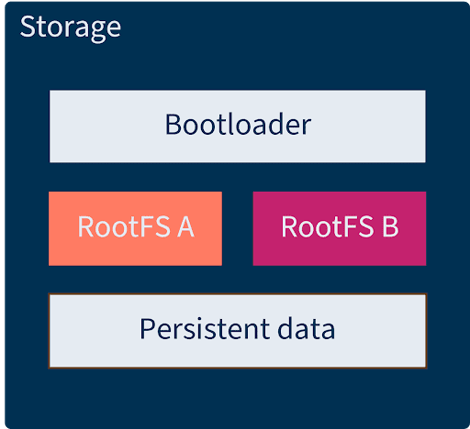
Adding structured system partitioning
Structured system partitioning can also optimize OTA update reliability, including:
- Splitting system components: Separating the boot directory, root file system, and application into distinct partitions with A/B versions.
- Thorough testing: Simulating failure scenarios to verify successful rollbacks and avoid bricked devices.
- Defining update confirmation criteria: Establishing conditions for marking updates as successful, such as network connectivity and proper execution of critical applications.
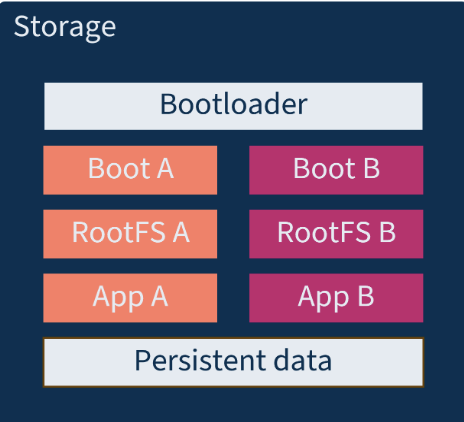
A/B Partitioning best practices
When implementing A/B partitioning for OTA updates, the following best practices are essential to ensuring reliability and minimizing disruptions. A well-structured partitioning strategy prevents data corruption and update failures, and reduces overall system downtime.
- Split Data thoughtfully:
- Avoid a single large data partition by separating containers, log data, and application data.
- Prevent data partition overflow, which can disrupt the update process.
- Bootloader considerations:
- Bootloaders are a single point of failure and should be treated as persistent components.
- Plan for bootloader updates early in the product lifecycle to minimize risks.
- Update confirmation process:
- Validate system startup and application execution.
- Ensure network connectivity remains intact post-update.
- Only confirm updates after passing all checks; otherwise, roll back to the previous version.
Storage and long-term considerations
Proactively planning for storage capacity is critical when implementing A/B partitioning. A/B updates require maintaining two full system images, which effectively doubles the storage demands. While modern devices with 512 MB or more typically support A/B partitioning, engineering teams should account for future firmware growth to prevent system lockups or update failures caused by insufficient storage space.
Beyond technical implementation, A/B partitioning plays a broader role in ensuring long-term system health and maintainability. Structuring the update process properly can reduce the risk of failures, strengthen security postures, and support compliance with evolving regulatory requirements. Organizations that adopt these practices position themselves to manage growing complexity while improving scalability, resilience, and reliability over time.
Choosing the right OTA strategy for security and scalability
As Holzmayr notes, many companies attempt to build their own OTA update solutions, only to find that they require far more time and effort than expected. For organizations with complex product requirements or security-sensitive deployments, standardized OTA solutions can reduce development overhead, improve long-term maintainability, and offer advanced capabilities that are difficult to replicate in-house.
A robust, secure, and scalable open-source OTA update solution is designed to simplify firmware and software updates across various devices. Capabilities include:
- Seamless A/B partitioning support: Structured updates with built-in rollback ensure devices remain operational even if updates fail.
- Secure updates: Cryptographic signing and end-to-end encryption protects the integrity and confidentiality of software artifacts.
- Compliance-ready: Support regulatory requirements like the CRA and RED with a security-focused design, audit and reporting features, and update tracking.
- Flexible deployment: Accommodate both cloud and on-premise environments for diverse operational requirements.
Moving towards standardization embraces best practices
The embedded industry needs to move away from isolated homegrown solutions and instead standardize on open, reliable, and secure OTA update methods. A/B partitioning is a fail-safe approach to OTA updates, ensuring that devices remain functional even if an update fails. By writing updates to an inactive partition before activation, products can maintain stability, security, and compliance with evolving regulatory standards.
As emphasized throughout Embedded World 2025, fragmentation continues to slow innovation across the ecosystem. Standardizing on update mechanisms like A/B partitioning is a critical step toward reducing long-term maintenance burdens and building a more cohesive, future-ready embedded landscape.
Want to dive deeper into how fragmentation affects development teams?
Explore our report: The Hidden Costs of Homegrown Update Systems
Continuing the conversation? Meet the Mender team at Embedded World North America in Anaheim, California this fall. We’ll be sharing more on secure OTA updates, standardization, and best practices for embedded systems.
Recent articles
The reach of AI: Digital, edge, physical, and beyond
The power of over-the-air (OTA) updates in patch management
Helm chart architectural changes: What, why, and how it affects you
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.




