What is Reverse SSH Tunneling and how does it work?
Want an easy way to SSH to a device behind a firewall but don’t want to set up a VPN? Welcome to the pragmatic person’s approach - Reverse SSH tunneling.
If you’re reading this you’ve probably heard of SSH, the cryptographic network protocol usually running on port 22 which allows you access to the shell of a remote machine.
In the most basic form, you use the SSH client on your workstation to connect to the SSH server on the remote side. By this act you form an SSH connection between the two.
What’s an SSH tunnel and how does it differ from a connection?
Let’s zoom out for a second and ask what a tunnel is in a general sense. It’s something you dig out to allow the road to continue through an obstacle. It has an entry point and exit point.
Let’s try to broaden that concept and say that a ferry transporting cars across some body of water is in a sense also acting as a tunnel. It’s allowing the road to pass over an obstacle. It has a source port and a destination one.
The ferry is also running on its own naval route (connection) between two ports. So a connection (road for cars) is being tunneled through another connection (naval route of the ferry).
An SSH tunnel is an SSH connection that serves as a ferry for other SSH connections allowing them to reach places they normally couldn’t.
What’s reversed in a reverse SSH tunnel?
We have to first define what the direction of a tunnel means. To follow up with the ferry analogy, a “direction of a tunnel” is defined by the direction of the ferry in relation to the dock which created the naval route.
Say port A wants to have a ferry line with port B. They buy a ferry, do all the bureaucracy and cars are now flowing from A->B. This is a normal tunnel.
A reverse tunnel is when port A sets everything up but their ferry is only taking people from B->A. So the ferry you board in port B is the only way to access port A. And port A created that naval route. Does it make sense for port A to do this? Yes, if it’s surrounded by cannons that will shoot down every ferry or car that tries to reach it by any other means.
How does this translate to SSH?
A reverse SSH tunnel is a method of allowing an SSH connection (cars) to an SSH server behind a firewall (port A).
A server behind the firewall usually means that either no incoming connection from the Internet to the server will be allowed and that the local IP address of the server isn’t a valid address on the Internet (due to a process called NAT - Network Address Transition).
This can happen because the “firewalled” server (port A) initially creates a reverse SSH tunnel (ferry naval route) to an arbitrary port on a publicly available server (port B). Making a regular SSH connection to that public server tunnels you to the “firewalled” server.
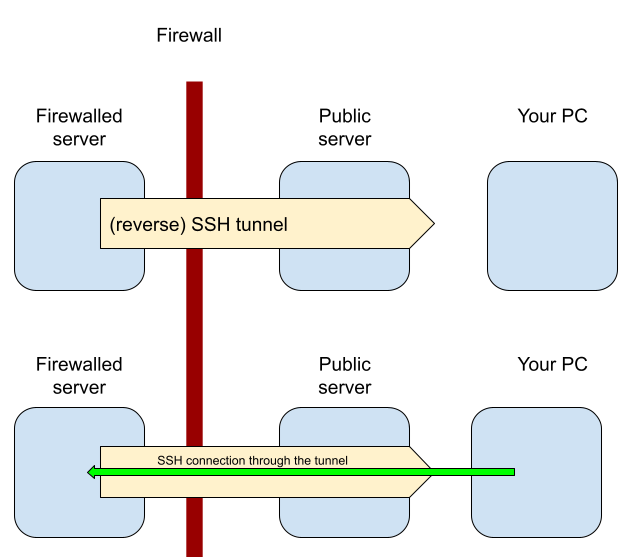
It’s reversed because the “firewalled” server did an outbound SSH connection to create a tunnel which is then used for establishing inbound ssh connections.
Mender Remote terminal
Mender is an open source software update management solution for IoT devices and has Remote terminal as an optional add-on (as part of the Troubleshoot add-on package). Mender's Remote terminal does not rely on SSH, but rather uses a simple bidirectional channel to transmit terminal characters over an existing secure Websocket connection.
If you need both to keep your software updated as well as shell access, Mender's Remote terminal may be a simpler solution for you. Read more here.
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.


