One of the biggest challenges in IoT security is the risk posed with an insecure software update process. Updates are critical for maintaining security on connected devices as the software on these devices will become outdated during their lifetime and vulnerabilities are certain to arise if left in their initial states. Therefore a secure, risk tolerant and efficient update mechanism must be at the core of each product development team from the inception of the project to end of life.
To design a secure software update process, a variety of attack vectors need to be taken into account and solutions needed to be identified to defend against these attacks. To ensure a security-by-design philosophy in the software update framework enterprises should adhere to three pillars of trust that look to protect people, devices and software (figure 1).
Figure 1. Mender's three pillars of trust in managing connected devices. 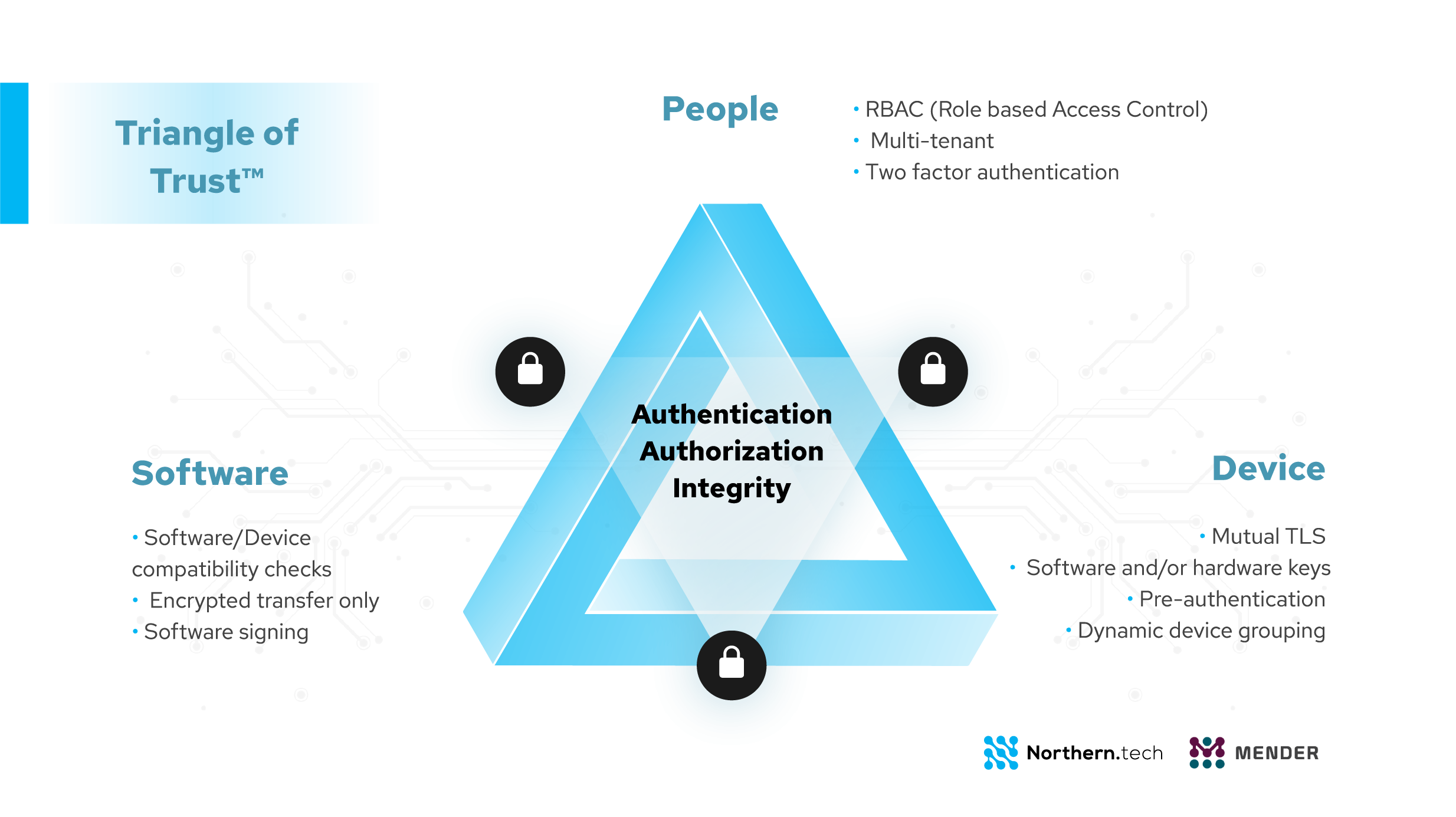
Enterprises running large scale complex operations and computing applications need to be certain that unauthorized users can’t compromise the system by deploying an unauthorized update to the device fleet. An example of this could be seen in the TRITON attack case where a number of publicly identified malicious software families targeted industrial control systems. The malware contained executable code that once deployed to the systems, caused total disruption of the operation. In this case, the malicious actor used a remote terminal access to an engineering workstation and deployed the TRITON attack framework to reprogram the system controllers. Though it is difficult to know exactly how they gained access and if the workstations had too many privileges in terms of accessibility, it is possible that Role Based Access Control (RBAC) would have helped to significantly reduce the risk of unauthorized software deployments. If the attack was that the engineering workstation had an open session to the over-the-air (OTA) server which it used to deploy malicious software in a group then RBAC could have limited the impact of the damage by only allowing the attacker to deploy to a small group of control systems, or potentially none at all (if the engineering workstation did not have deployment rights).
Additional layer for preventing security threats could be with audit logs , with which in the case of the TRITON attack if implemented one could see which user created a remote terminal session to which device and when. Audit logs can be an important basis for increasing security, policy compliance and accountability by logging events that can later be analyzed in case of operational incidents. Audit logs can be a great tool to do post mortem analysis in order to prevent similar malware attacks in the future. In the TRITON case where the engineering workstations were dismantled, the audit log can be used to check the software deployments that were made against them and who created the deployment and when.
The underlying criterion is that any device connected to the internet is vulnerable to security attacks and protecting them lies precisely in a framework that must consider the three pillars of trust.
Mender has recently launched the Remote terminal feature in open source. This feature provides added-value to Mender Enterprise customers who have access to RBAC and Audit logs features. Sign up for a free trail of Mender Enterprise to evaluate all of its features.
Recent articles
New Mender experimental AI-enabled feature
Mender in 2025: A year in review with compliance, security, and AI-driven growth
What’s new in Mender: Enhanced delta updates and user experience
Learn why leading companies choose Mender
Discover how Mender empowers both you and your customers with secure and reliable over-the-air updates for IoT devices. Focus on your product, and benefit from specialized OTA expertise and best practices.



